Platform
Platform
Everything you need to run a secure global network—in a single system.
Solutions
Solutions
Learn how our solutions were designed to help you scale your IT resources
Company
CommandLink
Let's talk about how we can help you!
Partners
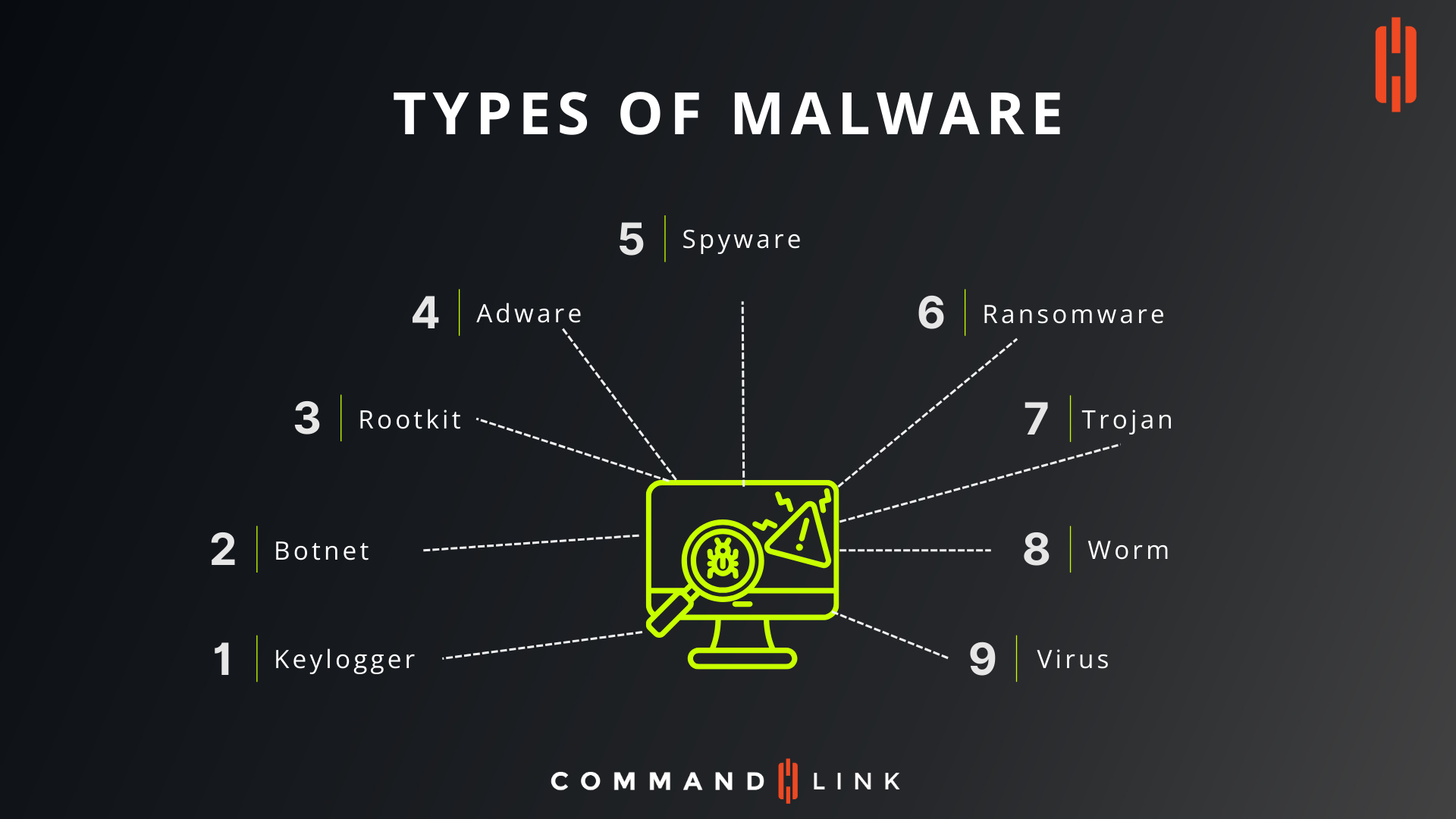
What is a Keylogger and How Does it Threaten Cybersecurity?
Keyloggers are a type of malware designed to record keystrokes on a victim's device, capturing sensitive information such as passwords, credit card numbers, and personal communications. This data is then sent back to the attacker, who can use it for malicious purposes, including identity theft or unauthorized access to systems. Keyloggers can be hardware-based, plugged directly into the device, or software-based, running invisibly in the background. The stealthy nature of keyloggers makes them particularly dangerous, as they often go undetected by the victim until significant damage has been done.
How Do Botnets Compromise Network Security?
Botnets are networks of infected computers, or "bots," controlled remotely by an attacker. These bots can be used for a variety of malicious activities, such as launching distributed denial-of-service (DDoS) attacks, sending spam, or spreading other types of malware. The vast scale at which botnets operate makes them a powerful tool for cybercriminals, capable of overwhelming even large networks and causing significant disruptions. Botnets often spread through phishing emails or vulnerabilities in software, and once a device is compromised, it becomes part of the botnet without the owner's knowledge.
What are Rootkits and Why are They Difficult to Detect?
Rootkits are a type of malware designed to gain unauthorized root-level access to a computer or network while hiding its presence. They can modify system files, access sensitive information, and allow attackers to control the device remotely. What makes rootkits particularly dangerous is their ability to conceal themselves from antivirus software and system administrators, making detection extremely difficult. Rootkits often enter a system through malicious software downloads or exploited vulnerabilities in the operating system. Because they operate at the core of the system, removing rootkits can be a complex and risky process.
How Does Adware Impact User Experience and Privacy?
Adware is a type of malware that automatically displays or downloads advertisements on a victim's device. While not always malicious, adware can be intrusive, slowing down devices and causing unwanted pop-ups or redirects to potentially harmful websites. In some cases, adware may also track user behavior, collecting data on browsing habits and personal information without the user's consent. This data can be sold to advertisers or used for targeted phishing attacks. Although adware is often bundled with legitimate software, it can be difficult to remove, leading to a degraded user experience and potential privacy concerns.
What is Spyware and How Does it Infiltrate Personal Data?
Spyware is a type of malware designed to gather information about a person or organization without their knowledge and send it to the attacker. This can include anything from tracking browsing history to recording passwords and capturing screenshots. Spyware often infiltrates devices through phishing emails, malicious websites, or software vulnerabilities. Once installed, it can be difficult to detect, as it operates silently in the background. The stolen data is typically used for identity theft, financial fraud, or corporate espionage, making spyware a serious threat to both individual privacy and organizational security.
What Makes Ransomware One of the Most Dangerous Types of Malware?
Ransomware is a type of malware that encrypts the victim's files, rendering them inaccessible until a ransom is paid to the attacker. Ransomware attacks have become increasingly common and sophisticated, targeting individuals, businesses, and even critical infrastructure. The encrypted files are often crucial to the victim's operations, creating a sense of urgency to pay the ransom, which is usually demanded in cryptocurrency to maintain anonymity. Ransomware can spread through phishing emails, infected websites, or vulnerabilities in software, and once it takes hold, it can be challenging to remove without paying the ransom or restoring from a backup—if one exists.
What are Trojans and How Do They Deceive Users?
Trojans, or Trojan horses, are a type of malware that disguises itself as a legitimate program or file to trick users into installing it on their devices. Once activated, Trojans can perform a variety of malicious actions, such as stealing data, creating backdoors for other malware, or taking control of the system. Unlike viruses or worms, Trojans do not replicate themselves but rely on the user to spread them by sharing the infected file. The deceptive nature of Trojans makes them a popular tool for cybercriminals, often used in phishing attacks or bundled with pirated software.
How Do Worms Spread Across Networks and What Damage Can They Cause?
Worms are a type of self-replicating malware that spreads across networks without the need for user interaction. Once a worm infects a device, it automatically searches for other vulnerable systems to infect, often spreading rapidly across an entire network. Worms can cause significant damage by consuming bandwidth, overloading servers, or delivering payloads that delete or corrupt files. Unlike viruses, worms do not require a host file to spread, making them particularly dangerous in networked environments. The ability of worms to spread autonomously and quickly makes them a significant threat to both individual systems and large-scale networks.
What is a Computer Virus and How Does it Differ from Other Types of Malware?
A computer virus is a type of malware that attaches itself to a legitimate program or file and spreads to other devices when the infected program or file is shared. Viruses can cause a wide range of damage, from corrupting data and stealing information to crashing entire systems. Unlike worms, which spread independently, viruses require some form of user interaction, such as opening an infected email attachment or running a compromised program. Viruses are one of the oldest forms of malware, but they continue to evolve, making them a persistent threat in the digital landscape.