Platform
Platform
Everything you need to run a secure global network—in a single system.
Solutions
Solutions
Learn how our solutions were designed to help you scale your IT resources
Company
CommandLink
Let's talk about how we can help you!
Partners
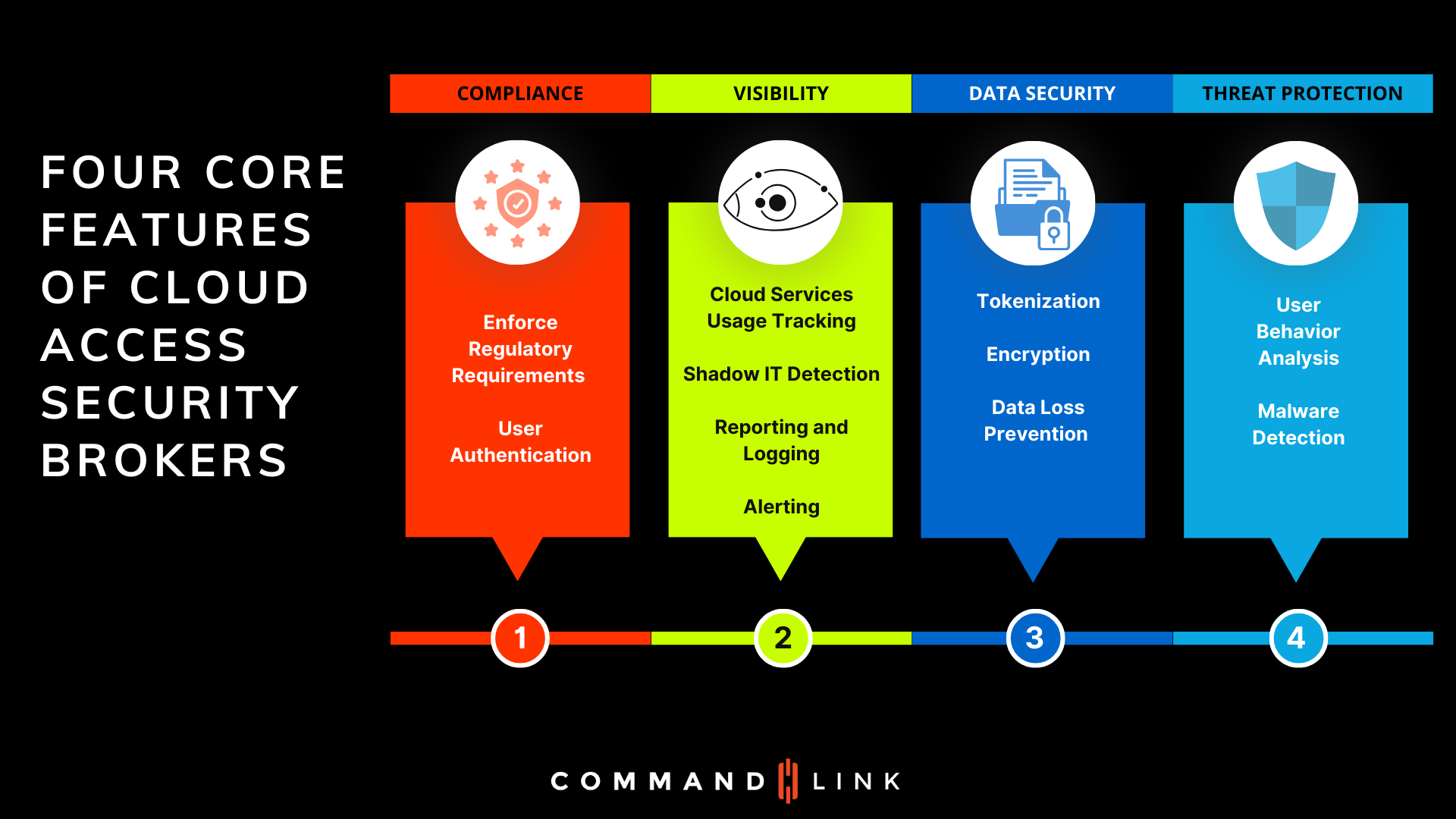
What Are the Core Features of Cloud Access Security Brokers?
As organizations increasingly adopt cloud services, ensuring the security of data and compliance with regulations becomes a critical challenge. Cloud Access Security Brokers (CASBs) play a vital role in securing cloud environments by providing a set of core features that address compliance, visibility, data security, and threat protection.
How Do CASBs Ensure Compliance?
Compliance is a cornerstone of cloud security, and CASBs are designed to enforce regulatory requirements across cloud services. They offer robust user authentication mechanisms that verify user identities before granting access to sensitive data. By ensuring that only authorized users can access critical information, CASBs help organizations meet industry regulations and avoid costly fines.
Why Is Visibility Important in Cloud Security?
Visibility into cloud service usage is essential for maintaining control over organizational data. CASBs provide comprehensive tracking of cloud services, including the detection of Shadow IT—unauthorized applications that can pose security risks. Through detailed reporting, logging, and real-time alerting, CASBs give IT teams the insights they need to manage cloud usage effectively and respond to potential issues before they escalate.
What Role Does Data Security Play in CASBs?
Data security is a primary concern for any organization using cloud services. CASBs address this by offering advanced features such as tokenization and encryption. These technologies ensure that sensitive data is protected both at rest and in transit. Additionally, CASBs implement data loss prevention (DLP) strategies to safeguard against accidental or malicious data breaches, ensuring that critical information remains secure.
How Do CASBs Provide Threat Protection?
Threat protection is a crucial component of cloud security. CASBs employ sophisticated tools like user behavior analysis to detect anomalies that could indicate a security threat. By monitoring user activity for signs of unusual or unauthorized behavior, CASBs can identify and mitigate risks before they lead to a breach. Additionally, CASBs offer malware detection capabilities to protect cloud environments from malicious software that could compromise data integrity.