Platform
Platform
Everything you need to run a secure global network—in a single system.
Solutions
Solutions
Learn how our solutions were designed to help you scale your IT resources
Company
CommandLink
Let's talk about how we can help you!
Partners
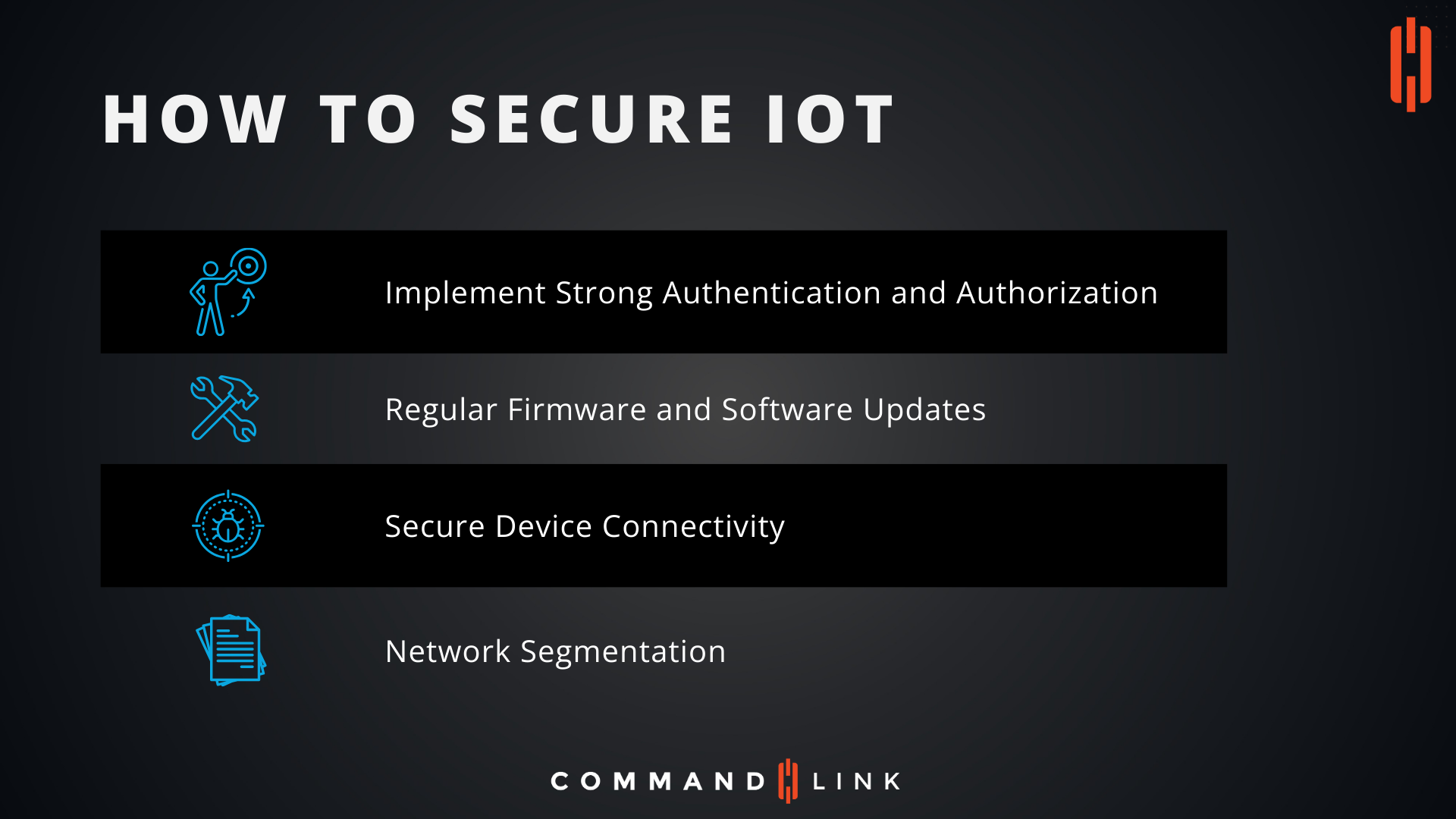
What Are the Best Practices for Securing IoT Devices?
As the Internet of Things (IoT) continues to expand, securing these devices has become increasingly critical. IoT devices are often vulnerable targets for cyberattacks due to their connectivity and the sensitive data they handle. Implementing strong security measures is essential to protect both the devices and the networks they are connected to. Below are some of the best practices for securing IoT devices.
How Can Strong Authentication and Authorization Protect IoT Devices?
Implementing strong authentication and authorization protocols is one of the most effective ways to secure IoT devices. This involves ensuring that only authorized users and devices can access the IoT system. Using multi-factor authentication (MFA) adds an additional layer of security by requiring users to provide two or more verification factors. Furthermore, role-based access control (RBAC) can be employed to limit access to sensitive data and functions within the IoT ecosystem, ensuring that users have only the permissions necessary for their role.
Why Are Regular Firmware and Software Updates Critical for IoT Security?
Keeping IoT devices up to date with the latest firmware and software is crucial for maintaining security. Manufacturers regularly release updates to patch security vulnerabilities and improve functionality. Failing to install these updates can leave devices exposed to known exploits. Automated update mechanisms can be implemented to ensure that devices are always running the latest version of their firmware and software, reducing the risk of exploitation due to outdated systems.
How Does Secure Device Connectivity Enhance IoT Security?
Ensuring secure device connectivity is essential to prevent unauthorized access and data breaches. Using encryption protocols such as Transport Layer Security (TLS) or Virtual Private Networks (VPNs) can protect the data transmitted between IoT devices and their controlling systems. Additionally, implementing secure communication channels can help prevent man-in-the-middle attacks and eavesdropping, which are common threats in IoT environments.
What Is the Role of Network Segmentation in IoT Security?
Network segmentation is a powerful strategy to enhance IoT security. By dividing a network into smaller, isolated segments, organizations can limit the spread of potential attacks and contain security breaches within a specific segment. This also allows for more granular control over network traffic, making it easier to monitor and manage IoT devices. Implementing firewalls and intrusion detection systems (IDS) between these segments can further strengthen security by detecting and blocking malicious activities.
Why Is IoT Security a Top Priority for Businesses?
IoT security is a top priority for businesses due to the increasing number of connected devices and the sensitive data they handle. A security breach in an IoT system can have far-reaching consequences, including data loss, operational disruption, and damage to a company's reputation. As IoT continues to grow, so does the complexity of securing these systems. Businesses must stay vigilant and proactive in their security measures to protect their IoT investments and ensure the safety and privacy of their data.
In conclusion, securing IoT devices requires a comprehensive approach that includes strong authentication and authorization, regular firmware and software updates, secure device connectivity, and network segmentation. By implementing these best practices, businesses can significantly reduce the risk of cyberattacks and protect their IoT infrastructure from potential threats.