Platform
Platform
Everything you need to run a secure global network—in a single system.
Solutions
Solutions
Learn how our solutions were designed to help you scale your IT resources
Company
CommandLink
Let's talk about how we can help you!
Partners
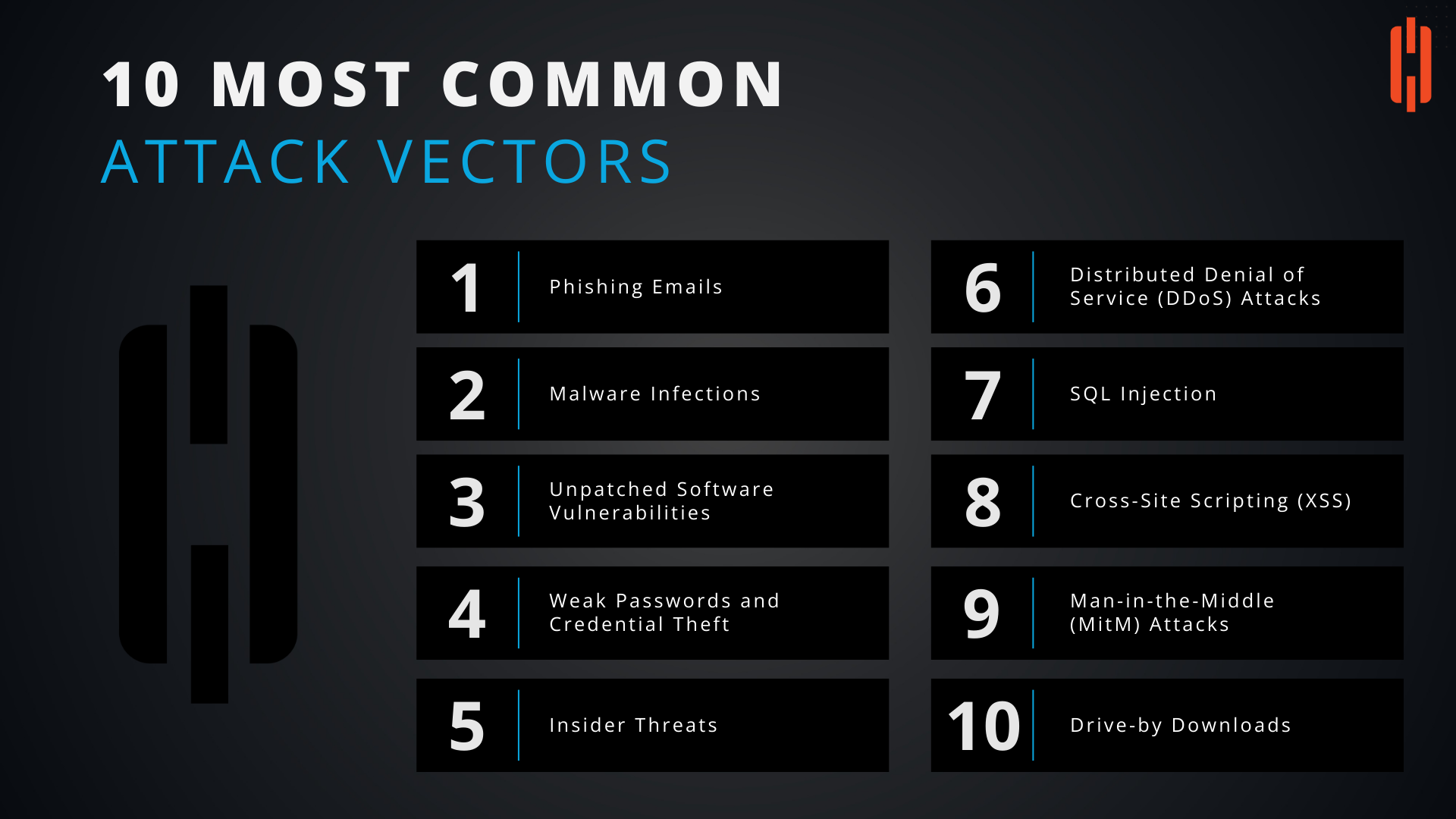
Understanding the 10 Most Common Attack Vectors in Cybersecurity
As the digital landscape continues to evolve, so do the methods cybercriminals use to exploit vulnerabilities in systems, networks, and applications. Understanding the most common attack vectors is essential for organizations to build effective defense strategies and protect their assets from potential threats. This article will explore the top 10 most common attack vectors that organizations should be aware of.
1. Phishing Emails
What is it?
Phishing emails are fraudulent messages that appear to come from a trusted source, tricking recipients into providing sensitive information such as login credentials, financial details, or personal data.
Why is it dangerous?
Phishing is one of the most prevalent and effective attack vectors because it exploits human psychology rather than technical vulnerabilities. A successful phishing attack can lead to unauthorized access to systems, data breaches, and financial loss.
Prevention:
2. Malware Infections
What is it?
Malware is malicious software designed to disrupt, damage, or gain unauthorized access to computer systems. It includes viruses, worms, trojans, ransomware, and spyware.
Why is it dangerous?
Malware can cause significant damage, including data theft, system crashes, and financial loss. Ransomware, a type of malware, can encrypt files and demand a ransom for their release.
Prevention:
3. Unpatched Software Vulnerabilities
What is it?
Unpatched vulnerabilities are security flaws in software that have not been fixed by updates or patches provided by the vendor.
Why is it dangerous?
Cybercriminals can exploit these vulnerabilities to gain unauthorized access to systems, steal data, or deploy malware.
Prevention:
4. Weak Passwords and Credential Theft
What is it?
Weak passwords are easily guessable or common passwords that provide inadequate protection. Credential theft occurs when attackers obtain login details through various means, such as phishing or keylogging.
Why is it dangerous?
Once attackers gain access to credentials, they can log into systems, steal data, and move laterally within the network, leading to widespread breaches.
Prevention:
5. Insider Threats
What is it?
Insider threats involve employees, contractors, or other trusted individuals who intentionally or unintentionally compromise the security of an organization.
Why is it dangerous?
Insiders often have legitimate access to sensitive information and systems, making it difficult to detect malicious activity.
Prevention:
6. Distributed Denial of Service (DDoS) Attacks
What is it?
DDoS attacks flood a targeted system or network with excessive traffic, overwhelming its resources and causing service disruptions.
Why is it dangerous?
DDoS attacks can render critical services unavailable, leading to operational disruptions, financial losses, and damage to reputation.
Prevention:
7. SQL Injection
What is it?
SQL injection is a type of cyberattack where attackers insert malicious SQL code into input fields to manipulate a database and access unauthorized data.
Why is it dangerous?
SQL injection can lead to unauthorized access to sensitive data, including customer information, financial records, and intellectual property.
Prevention:
8. Cross-Site Scripting (XSS)
What is it?
XSS is a web security vulnerability that allows attackers to inject malicious scripts into web pages viewed by users, potentially compromising their data or redirecting them to malicious sites.
Why is it dangerous?
XSS can lead to data theft, session hijacking, and the distribution of malware to website visitors.
Prevention:
9. Man-in-the-Middle (MitM) Attacks
What is it?
MitM attacks occur when attackers intercept and potentially alter communication between two parties without their knowledge.
Why is it dangerous?
MitM attacks can lead to data theft, unauthorized access, and the manipulation of communications, potentially compromising sensitive transactions.
Prevention:
10. Drive-by Downloads
What is it?
Drive-by downloads occur when a user unknowingly downloads malicious software simply by visiting a compromised website.
Why is it dangerous?
Drive-by downloads can result in the installation of malware, ransomware, or spyware on a user's device without their consent or knowledge.
Prevention:
Understanding these common attack vectors is the first step in fortifying an organization's cybersecurity posture. By implementing the appropriate security measures, educating employees, and staying vigilant, organizations can significantly reduce their risk of falling victim to these pervasive threats. As cyber threats continue to evolve, it is crucial to remain proactive in identifying and mitigating potential vulnerabilities in the digital ecosystem.