Understanding CASB Reverse Proxy
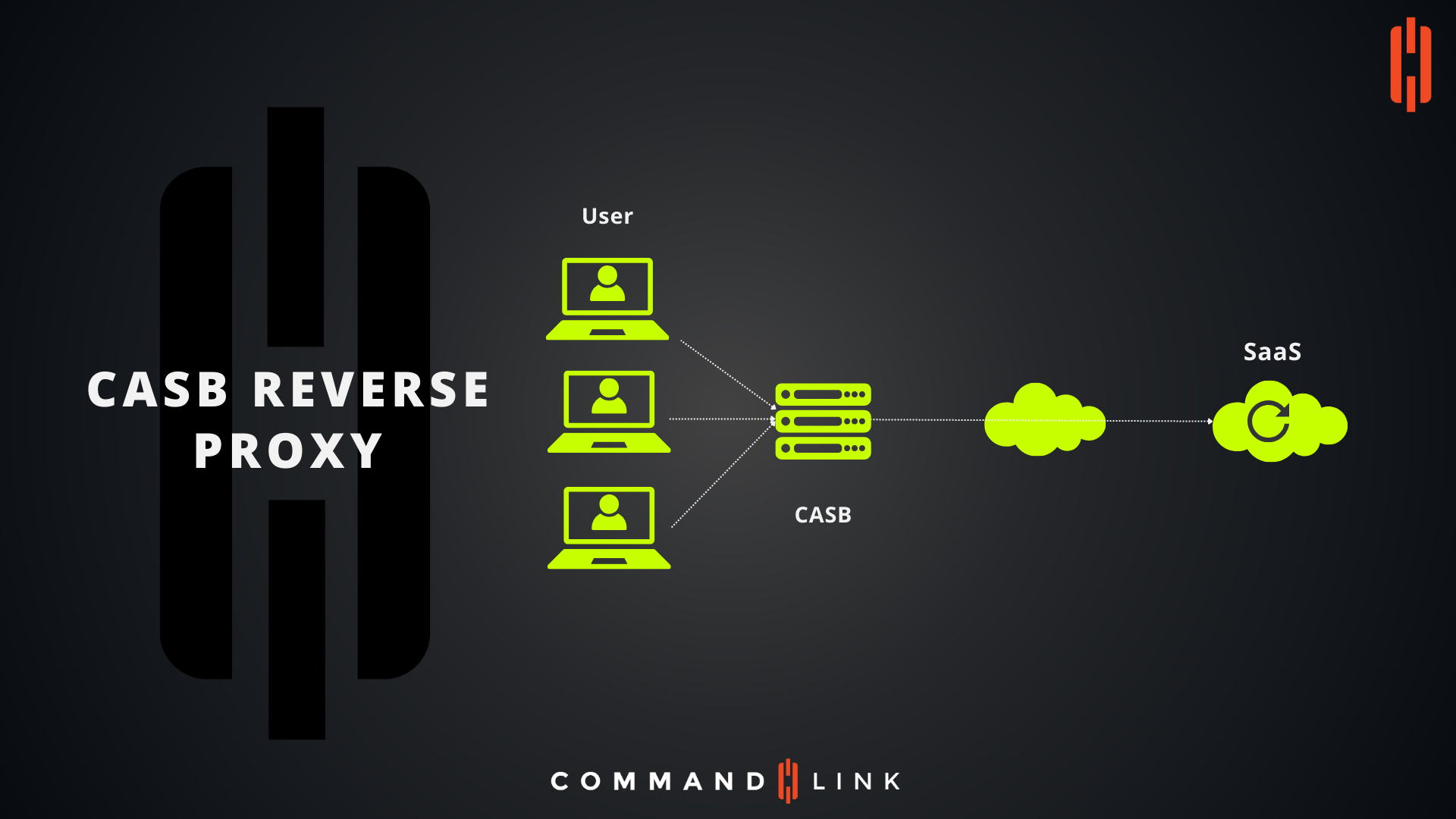
A Cloud Access Security Broker (CASB) is a security policy enforcement point positioned between cloud service consumers and cloud service providers to ensure that enterprise security policies are enforced when cloud-based resources are accessed. One of the common deployment modes of a CASB is the reverse proxy, which is highlighted in the provided diagram.
What is a CASB Reverse Proxy?
A CASB reverse proxy operates by intercepting traffic between users and the cloud services they are accessing. It functions as an intermediary that enforces security policies by evaluating and controlling the data that flows between users and cloud services.
Key Components and Workflow:
- User Devices: The diagram shows multiple users, each represented by a laptop. These users are trying to access cloud-based SaaS (Software as a Service) applications.
- CASB: The CASB sits between the users and the SaaS applications. All traffic destined for the cloud services passes through the CASB, where security policies are enforced. This includes data loss prevention, encryption, malware detection, and ensuring compliance with regulatory standards.
- SaaS Applications: These are the cloud-based services that the users are trying to access, such as CRM systems, collaboration tools, or storage services. The CASB ensures that only secure and compliant data interactions occur with these SaaS providers.
How CASB Reverse Proxy Works:
- Interception of Traffic: When a user attempts to access a SaaS application, the traffic is first routed through the CASB. Unlike a forward proxy, which handles outbound traffic, a reverse proxy deals with incoming requests to cloud services, making it ideal for controlling access and enforcing security policies in real-time.
- Policy Enforcement: The CASB evaluates the request against predefined security policies. This could include checking for unauthorized data sharing, ensuring that only allowed users can access specific services, or applying encryption to sensitive data before it leaves the corporate network.
- Secure Access: After the CASB enforces the necessary policies, the request is forwarded to the SaaS application. The response from the SaaS provider is also routed back through the CASB, ensuring that any data returned is subject to the same security controls.
Benefits of CASB Reverse Proxy:
- Enhanced Security: By controlling access to cloud services, the CASB can prevent unauthorized access, protect against data breaches, and ensure compliance with regulations.
- Visibility and Control: IT administrators gain visibility into cloud usage and can control access based on detailed policies that align with the organization’s security objectives.
- Protection of Sensitive Data: The CASB can enforce encryption and other data protection measures to ensure that sensitive information remains secure, even when stored in or accessed through cloud services.
- Compliance: By enforcing security policies, a CASB helps organizations comply with industry regulations such as GDPR, HIPAA, and others, reducing the risk of costly violations.
A CASB reverse proxy is a powerful tool for organizations looking to secure their cloud environments. By sitting between users and cloud services, it provides comprehensive control over data and access, ensuring that cloud interactions are secure, compliant, and in line with organizational policies. This setup is particularly useful in today’s cloud-first world, where sensitive data often flows between multiple cloud applications and services.