Understanding CASB Forward Proxy
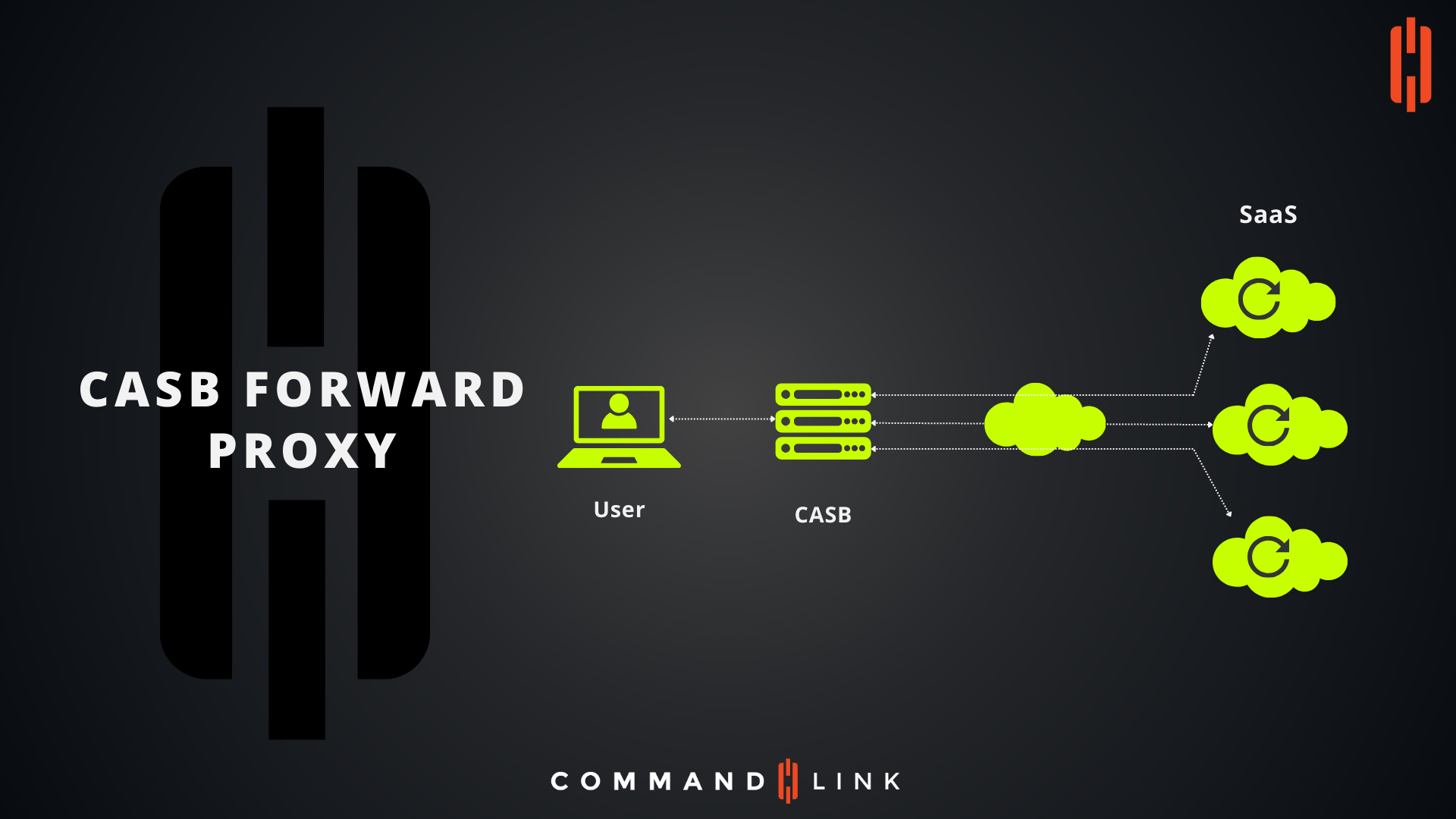
A Cloud Access Security Broker (CASB) is a security control point that acts as a gatekeeper between an organization's on-premises infrastructure and a cloud provider's infrastructure, enforcing security policies as data travels to and from the cloud. The forward proxy deployment mode, depicted in the diagram, is one of the common methods used by CASBs to monitor and secure cloud access.
What is a CASB Forward Proxy?
A CASB forward proxy works by sitting between users and the cloud services they are attempting to access. It intercepts and controls all outbound traffic to cloud applications, enforcing security policies before the data reaches the cloud.
Key Components and Workflow:
- User Devices: The diagram shows a user, represented by a laptop. This user initiates a request to access a cloud-based SaaS (Software as a Service) application.
- CASB: Positioned between the user and the cloud, the CASB in forward proxy mode intercepts the outbound traffic from the user. The CASB applies security policies such as encryption, data loss prevention, malware detection, and compliance checks before allowing the traffic to proceed to the cloud service.
- SaaS Applications: These are the cloud services the user wants to access, such as email, collaboration tools, or storage services. The CASB ensures that any interaction with these services adheres to the organization's security policies.
How CASB Forward Proxy Works:
- Traffic Interception: When a user attempts to access a cloud service, the request is routed through the CASB. Unlike the reverse proxy, which deals with incoming traffic to the cloud, the forward proxy focuses on outgoing traffic from the organization to the cloud.
- Policy Enforcement: As the CASB intercepts the traffic, it evaluates it against predefined security policies. This can include encrypting data before it leaves the organization, preventing sensitive information from being uploaded to unauthorized cloud services, and blocking access to risky or non-compliant cloud applications.
- Secure Access: Once the CASB has applied the necessary security policies, the traffic is forwarded to the SaaS application. The CASB also monitors the traffic returning from the cloud, ensuring that it complies with the organization's security requirements.
Benefits of CASB Forward Proxy:
- Comprehensive Data Protection: By controlling all outbound traffic to the cloud, the CASB ensures that sensitive data is protected from loss, theft, or unauthorized access. This is especially important for organizations that handle regulated data, such as healthcare records or financial information.
- Policy Compliance: The CASB enforces compliance with internal policies and external regulations by controlling how data is accessed and shared in the cloud. This helps organizations avoid costly fines and legal issues related to data breaches or regulatory violations.
- Visibility and Control: Organizations gain visibility into all cloud usage, including unsanctioned cloud services (shadow IT), allowing them to control access and ensure that only approved cloud applications are used.
- Threat Protection: The CASB can block access to known malicious sites and prevent the upload of malware to cloud services, reducing the risk of cyberattacks originating from or targeting cloud-based environments.
A CASB forward proxy is a vital component for organizations looking to secure their journey to the cloud. By monitoring and controlling outbound traffic to cloud services, it ensures that data remains protected and compliant with security policies, providing a secure gateway for cloud access. This deployment mode is particularly useful for organizations that want to maintain strict control over how their data is accessed, used, and shared in the cloud.