Platform
Platform
Everything you need to run a secure global network—in a single system.
Solutions
Solutions
Learn how our solutions were designed to help you scale your IT resources
Company
CommandLink
Let's talk about how we can help you!
Partners
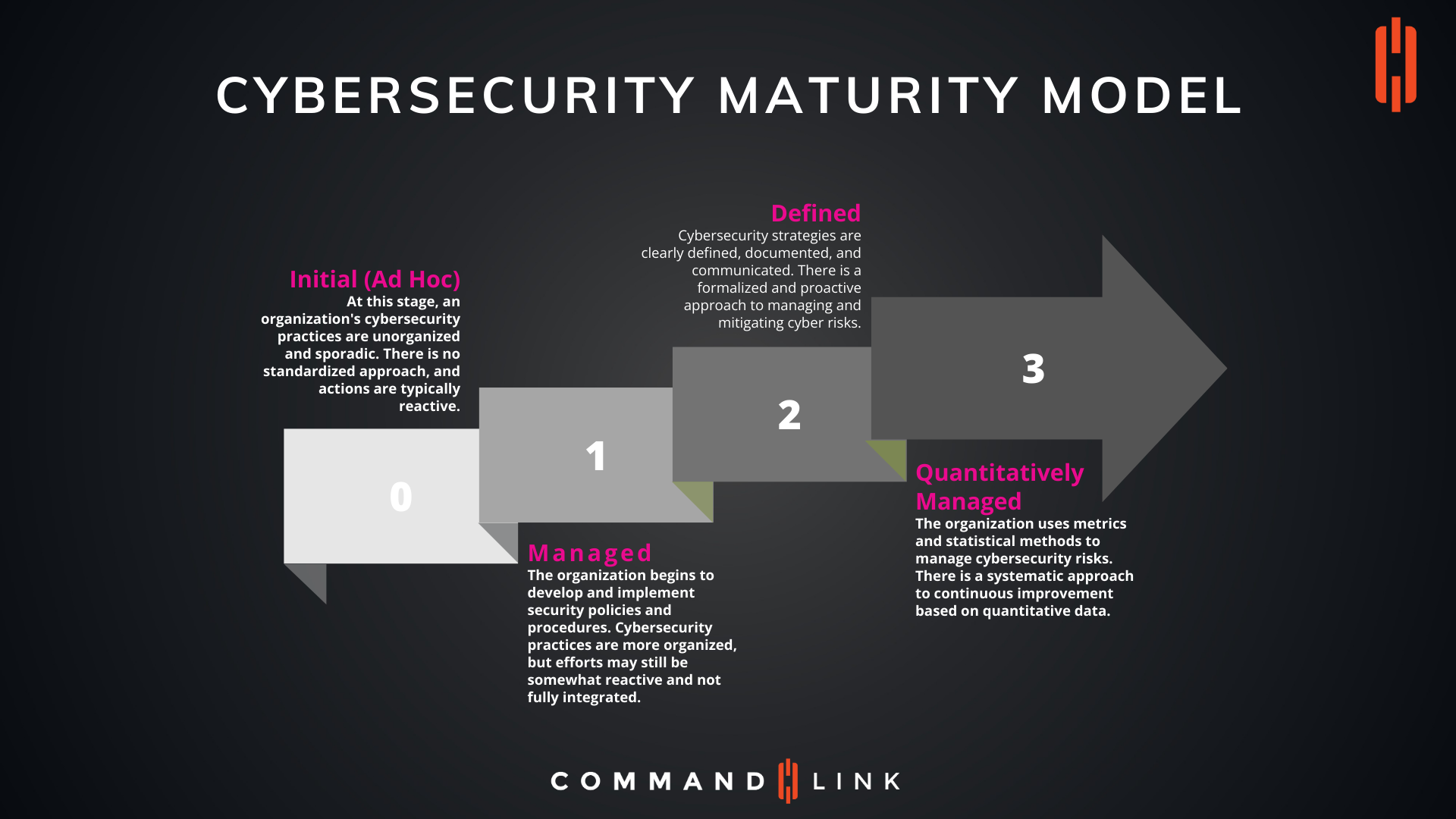
Navigating the Cybersecurity Maturity Model: A Strategic Approach to Managing Cyber Risk
In today's digital age, cybersecurity is no longer a secondary concern—it is a fundamental aspect of business operations. As organizations grow and evolve, so must their cybersecurity practices. The Cybersecurity Maturity Model (CMM) provides a structured approach to understanding and managing cybersecurity risks at different stages of organizational development. This article explores the stages of the CMM, guiding organizations on how to evolve their cybersecurity posture from ad hoc practices to a quantitatively managed, data-driven approach.
What is the Cybersecurity Maturity Model?
The Cybersecurity Maturity Model is a framework that helps organizations assess the effectiveness of their cybersecurity practices. It defines different levels of maturity, each representing a stage in the development and implementation of cybersecurity strategies and controls. The model emphasizes a continuous improvement process, encouraging organizations to advance through the maturity levels to achieve a more robust and proactive cybersecurity posture.
The Stages of the Cybersecurity Maturity Model
1. Initial (Ad Hoc) – Stage 0
Characteristics:
Challenges: Organizations at this stage often lack formalized cybersecurity policies and procedures. Security measures are implemented on an as-needed basis, which can lead to significant vulnerabilities. The absence of a cohesive strategy increases the likelihood of data breaches, system downtime, and compliance issues.
Next Steps: To move beyond the ad hoc stage, organizations should start by recognizing the importance of cybersecurity and allocating resources to develop a more structured approach. This includes creating basic cybersecurity policies and beginning to document processes.
2. Managed – Stage 1
Characteristics:
Challenges: While there is an improvement from the ad hoc stage, organizations at the managed stage still face challenges in fully integrating their cybersecurity practices. Security efforts may be inconsistent, and there is often a reliance on manual processes, which can be time-consuming and error-prone.
Next Steps: Organizations should focus on standardizing their cybersecurity practices across all departments and systems. This involves automating security processes where possible, conducting regular risk assessments, and ensuring that all staff members are aware of and adhere to security policies.
3. Defined – Stage 2
Characteristics:
Challenges: At the defined stage, organizations may struggle with the complexity of managing a comprehensive cybersecurity program. Ensuring that all components of the security strategy are aligned with business objectives and regulatory requirements can be challenging.
Next Steps: Organizations should aim to refine their cybersecurity strategies, ensuring that they are adaptable to changing threats and business needs. This includes regularly updating policies and procedures, investing in advanced security technologies, and fostering a security-aware culture throughout the organization.
4. Quantitatively Managed – Stage 3
Characteristics:
Challenges: Reaching the quantitatively managed stage requires significant investment in resources, including advanced security tools, skilled personnel, and robust data analytics capabilities. Organizations must also ensure that they can effectively interpret and act on the data they collect.
Next Steps: Organizations at this stage should continue to refine their use of data and analytics to drive decision-making. This includes developing key performance indicators (KPIs) for cybersecurity, conducting regular security audits, and using insights from data to continuously enhance security measures.
The Cybersecurity Maturity Model offers a roadmap for organizations to enhance their cybersecurity posture systematically. By understanding and progressing through the stages of the CMM, organizations can move from a reactive approach to a proactive, data-driven strategy that effectively manages cyber risks. As cybersecurity threats continue to evolve, it is crucial for organizations to remain vigilant, continuously assess their maturity level, and strive for improvement to protect their assets and maintain trust with stakeholders.