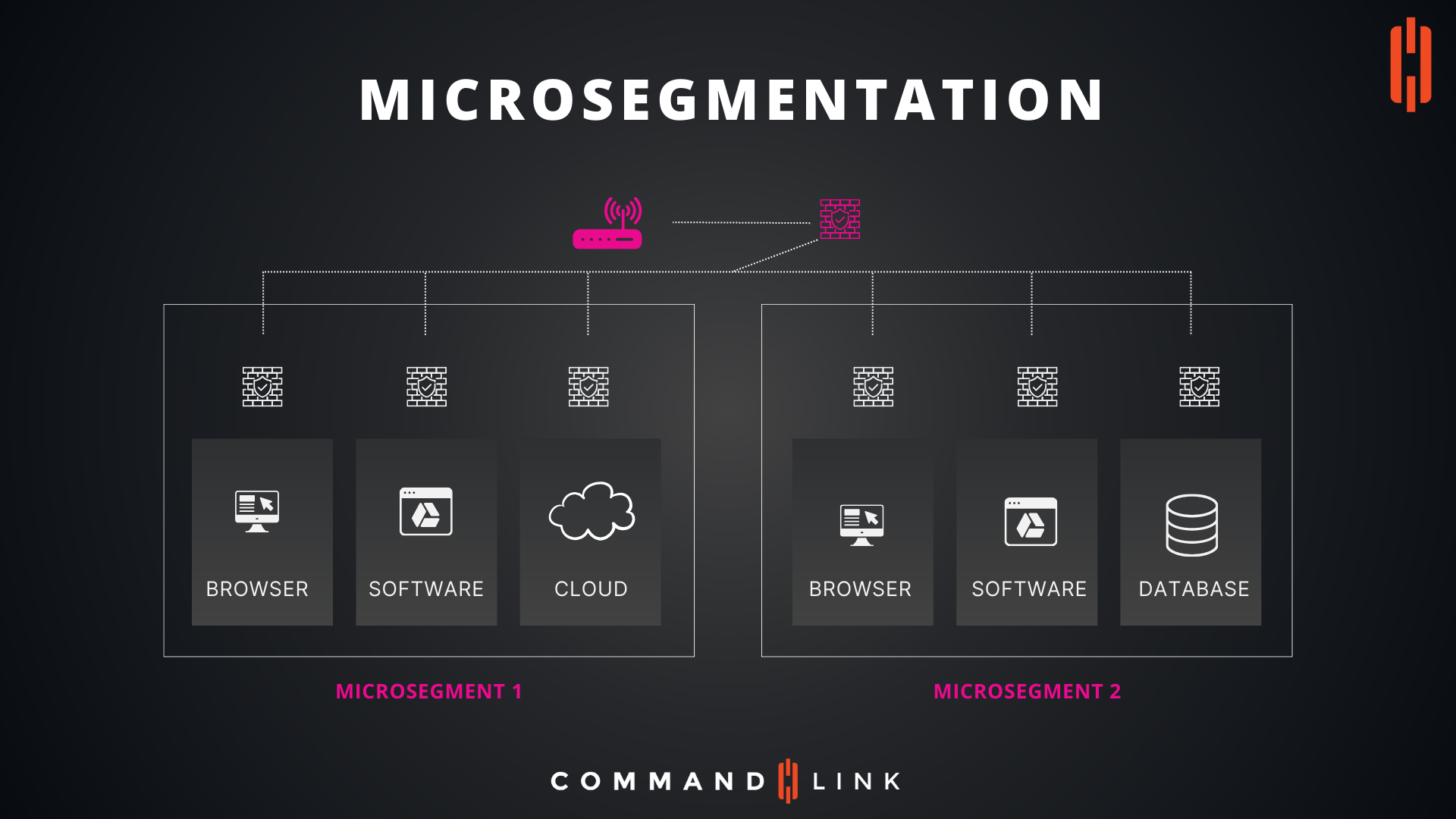
Microsegmentation: Enhancing Security Through Granular Network Segmentation
Microsegmentation is a powerful cybersecurity technique that divides a network into smaller, isolated segments, or "microsegments." This strategy allows organizations to implement more precise security controls, reducing the attack surface and limiting the potential impact of breaches. The image illustrates how microsegmentation works, depicting two distinct microsegments, each with its own set of resources and security controls. Let’s delve into the key concepts and benefits of microsegmentation.
What is Microsegmentation?
Microsegmentation involves creating secure zones within a network where each zone can have its own set of security policies. These policies are enforced by network firewalls, virtual firewalls, or other security appliances. Unlike traditional network segmentation, which might segment a network based on broad categories such as departments or functions, microsegmentation allows for more granular control, down to the individual application or workload level.
Components of the Microsegmentation Diagram
- Microsegments (Microsegment 1 and Microsegment 2)
- Function: Each microsegment represents a distinct, isolated portion of the network, containing specific resources such as browsers, software, cloud services, or databases. The resources within a microsegment can communicate with each other freely but are isolated from resources in other microsegments unless explicitly allowed by security policies.
- Benefits: This isolation helps prevent the lateral movement of threats within the network. If a breach occurs within one microsegment, it is contained, and the attacker cannot easily access resources in other microsegments.
- Security Controls (Firewalls)
- Function: Each microsegment is protected by its own set of security controls, typically implemented through firewalls or virtual firewalls. These controls enforce the security policies that govern which traffic is allowed to enter or leave the microsegment.
- Benefits: By applying security controls at the microsegment level, organizations can enforce strict access controls, monitor traffic closely, and quickly respond to suspicious activities. This approach enhances security by ensuring that only authorized users and applications can access sensitive data or critical systems.
- Connectivity Between Microsegments
- Function: The connectivity between microsegments is tightly controlled and monitored. Any communication between microsegments must pass through security controls that enforce the policies governing that interaction.
- Benefits: This controlled connectivity ensures that even if an attacker gains access to one microsegment, they cannot easily compromise other parts of the network. It also allows for secure interactions between different parts of the network, such as between a cloud service and a database, while maintaining strict security controls.
Benefits of Microsegmentation
- Enhanced Security: By isolating resources and applying granular security policies, microsegmentation significantly reduces the attack surface and limits the potential impact of breaches.
- Improved Compliance: Microsegmentation helps organizations meet regulatory requirements by ensuring that sensitive data is isolated and protected according to strict security standards.
- Reduced Lateral Movement: Microsegmentation prevents attackers from moving laterally across the network, containing breaches and protecting critical assets from compromise.
- Flexibility and Scalability: Microsegmentation allows organizations to apply security policies dynamically, adapting to changes in the network, such as the addition of new applications or services, without disrupting operations.
Microsegmentation is a crucial technique for modern network security, offering a higher level of control and protection than traditional network segmentation methods. By isolating different parts of the network and enforcing granular security policies, organizations can better protect their critical assets, reduce the risk of widespread breaches, and ensure compliance with regulatory standards. As cyber threats continue to evolve, adopting microsegmentation will be an essential part of a robust cybersecurity strategy.