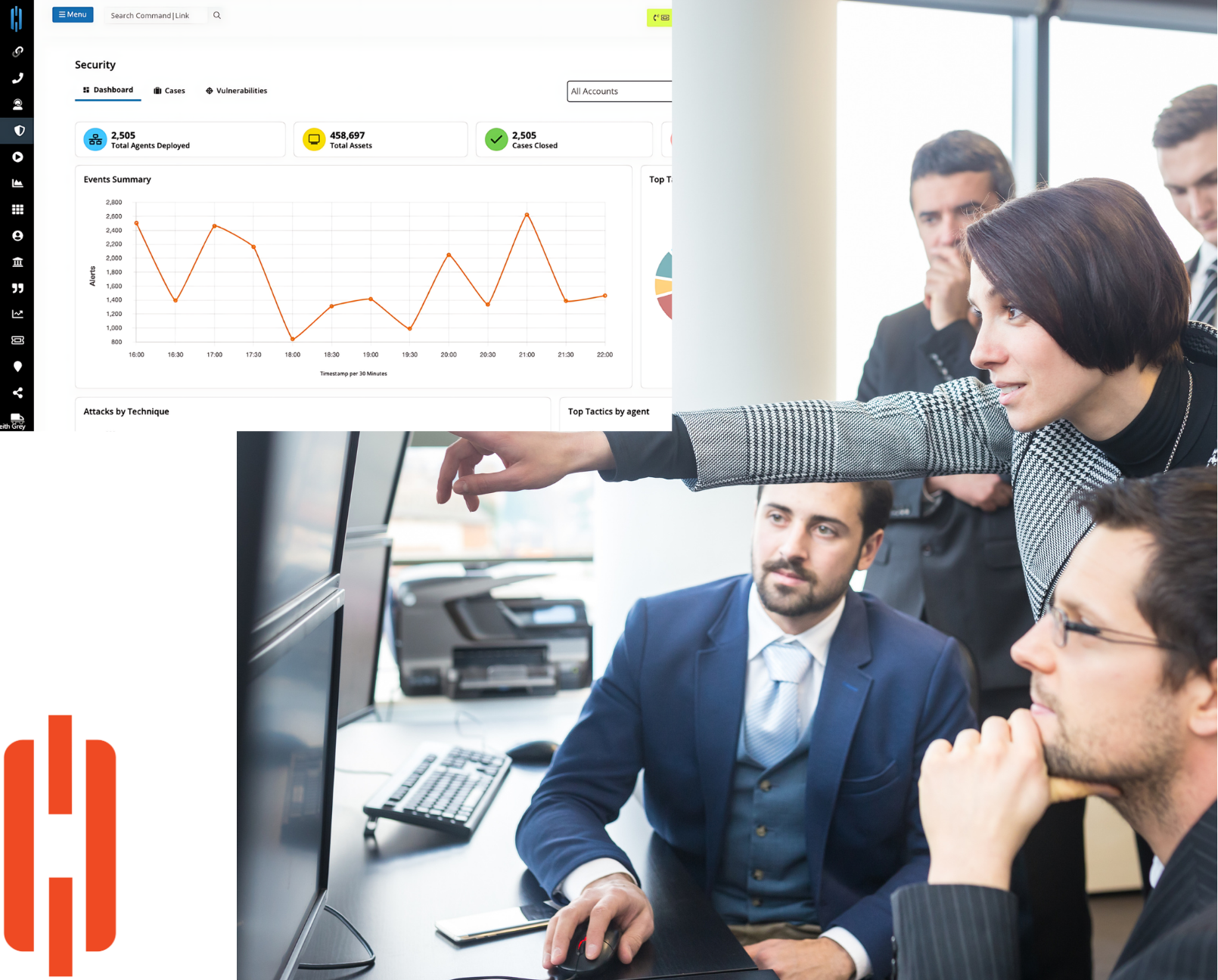
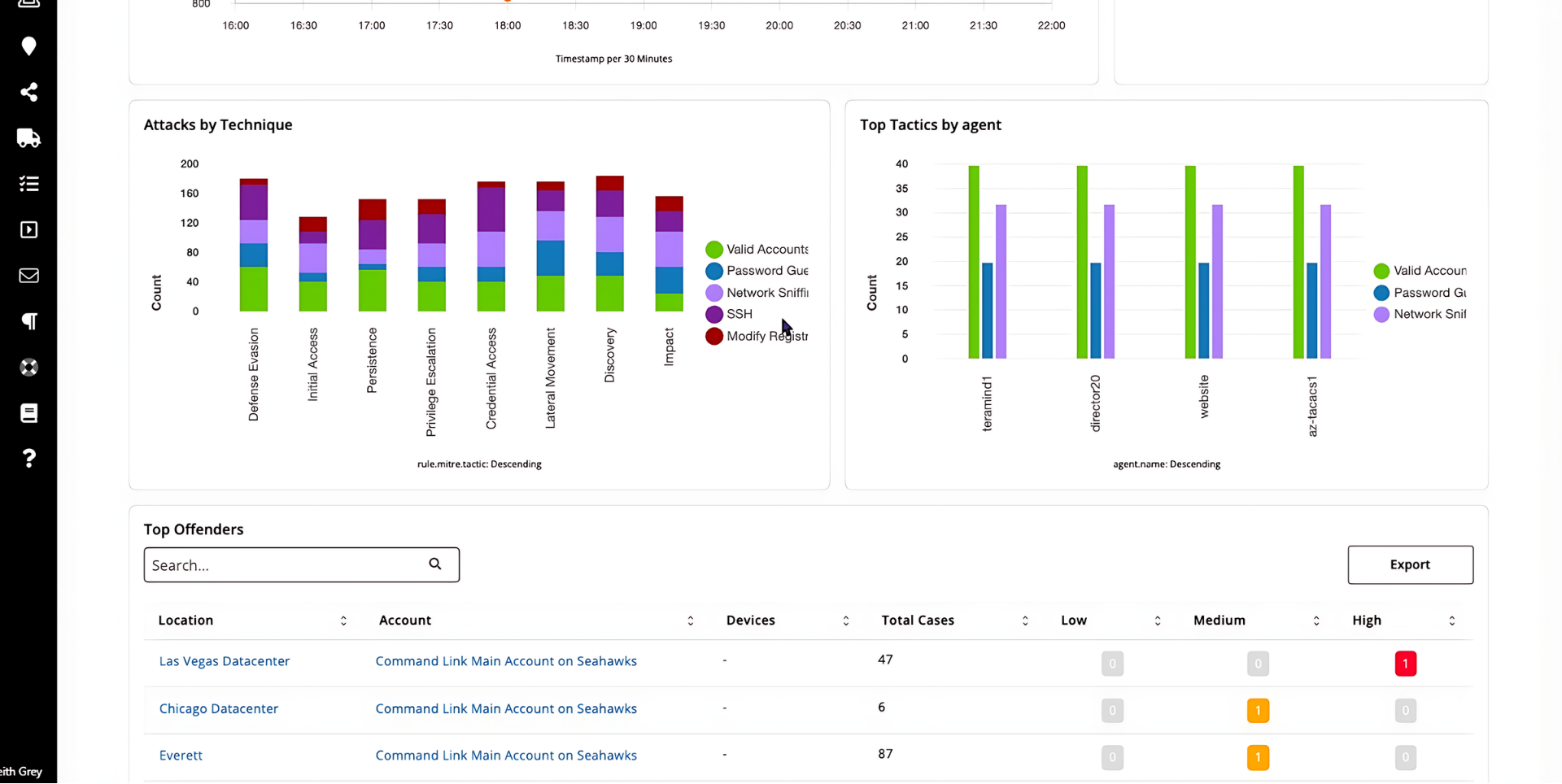
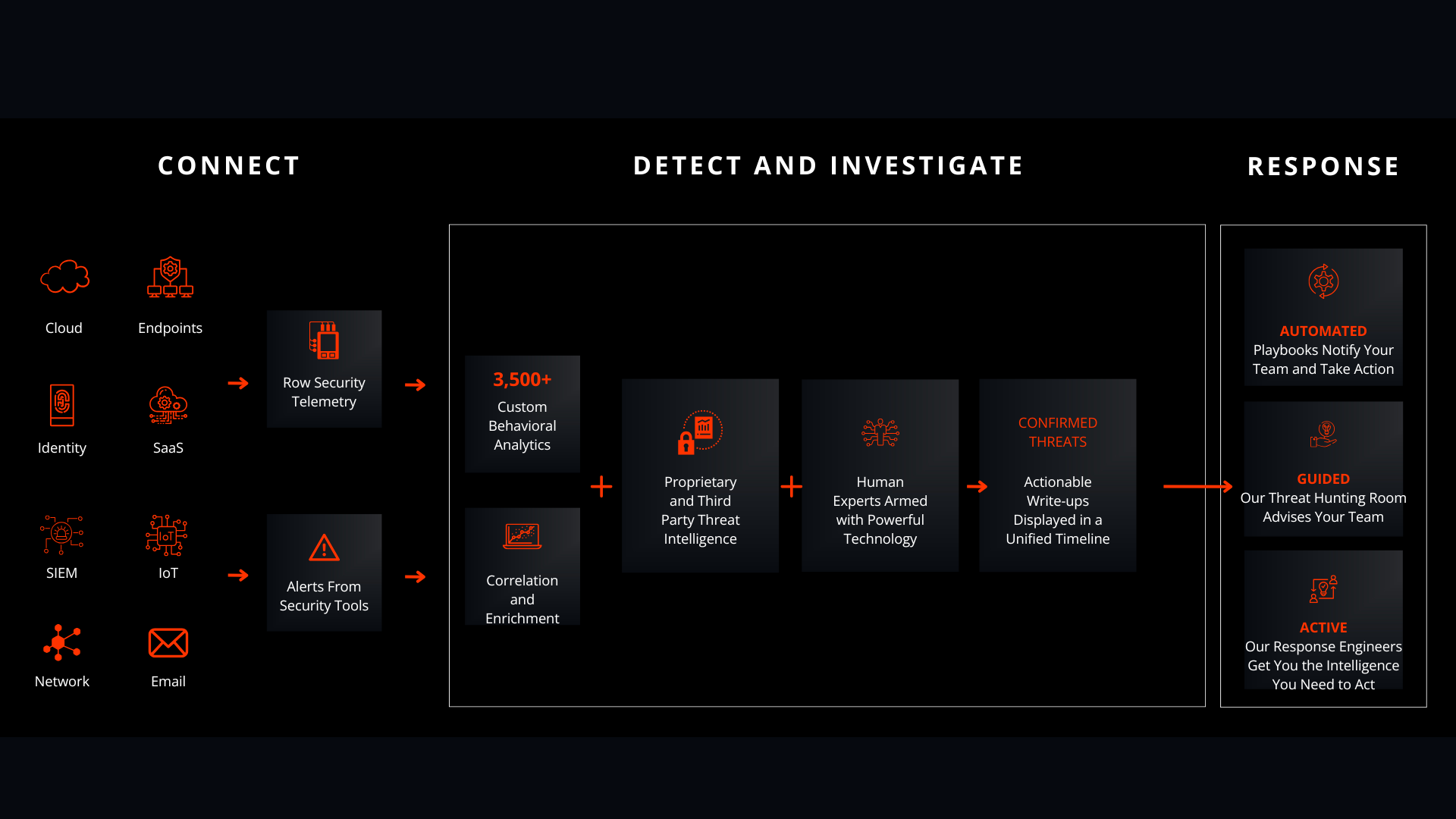
Threat Level Strategy
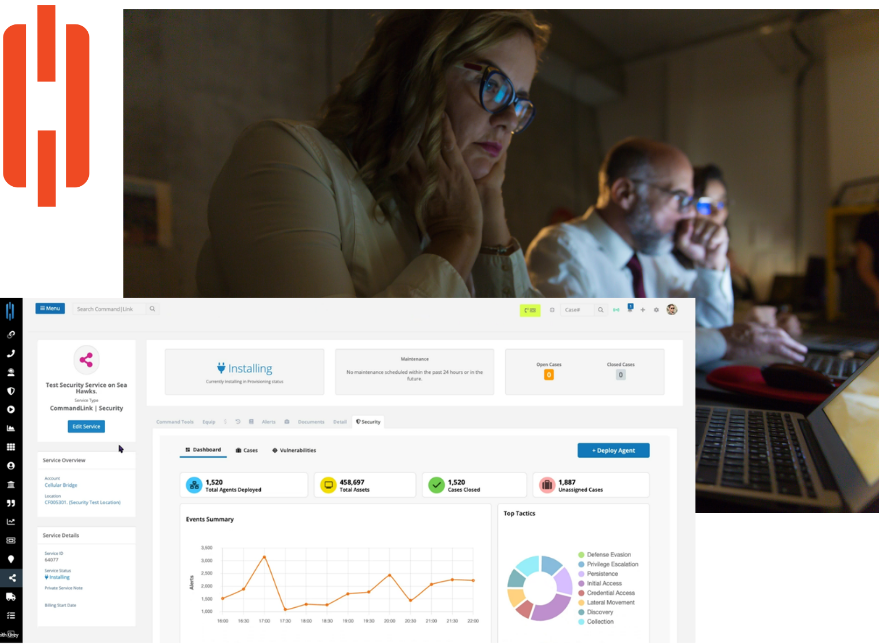
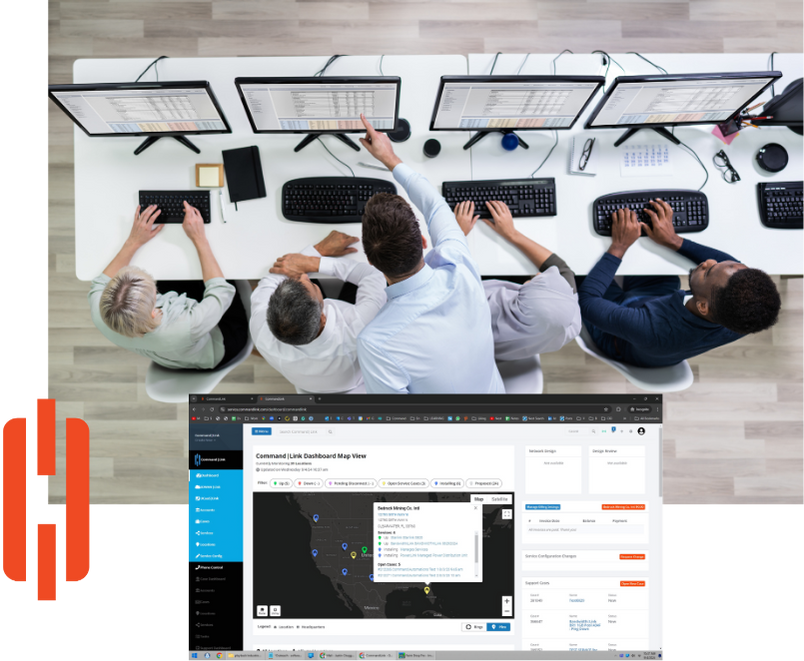
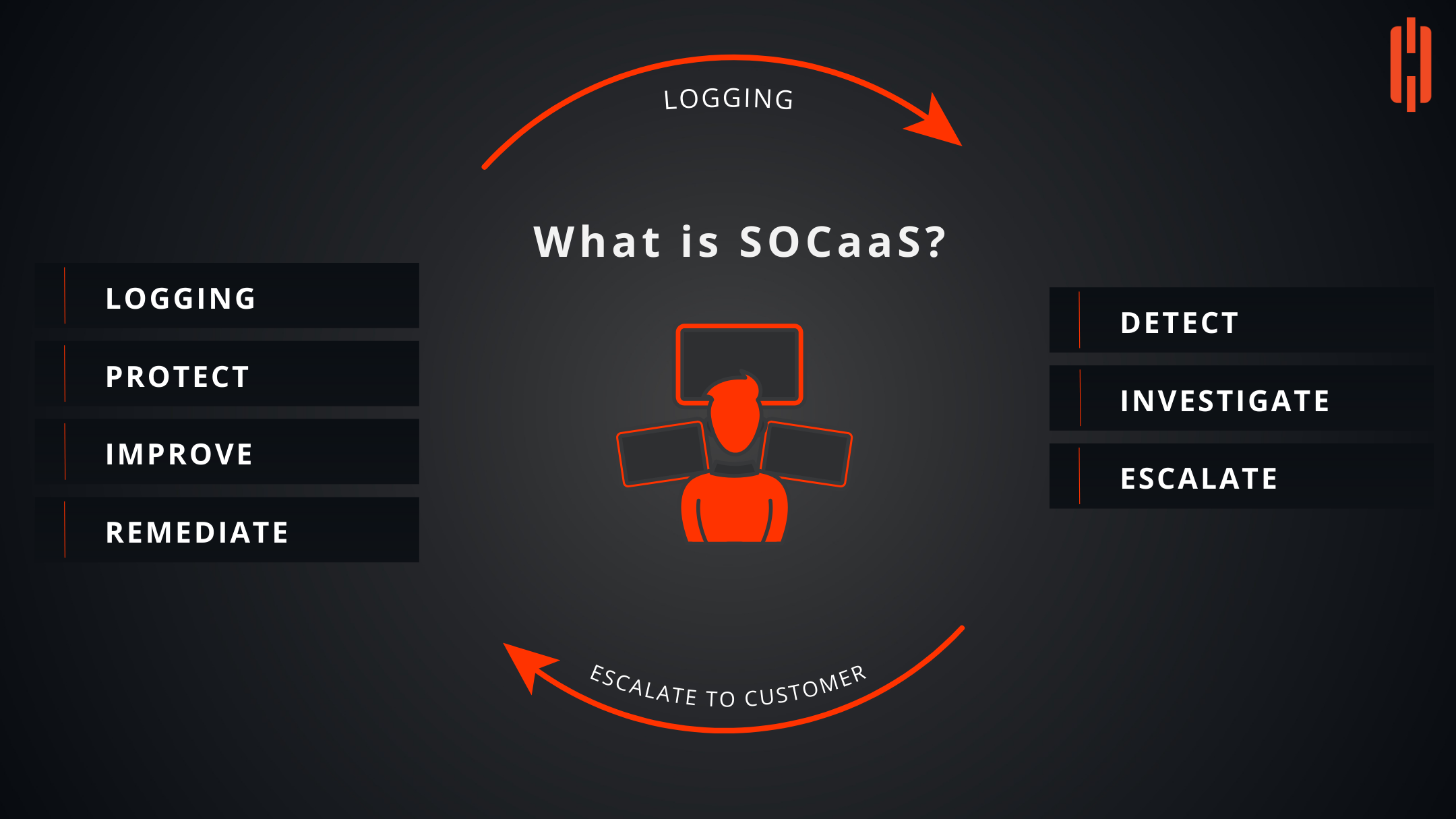
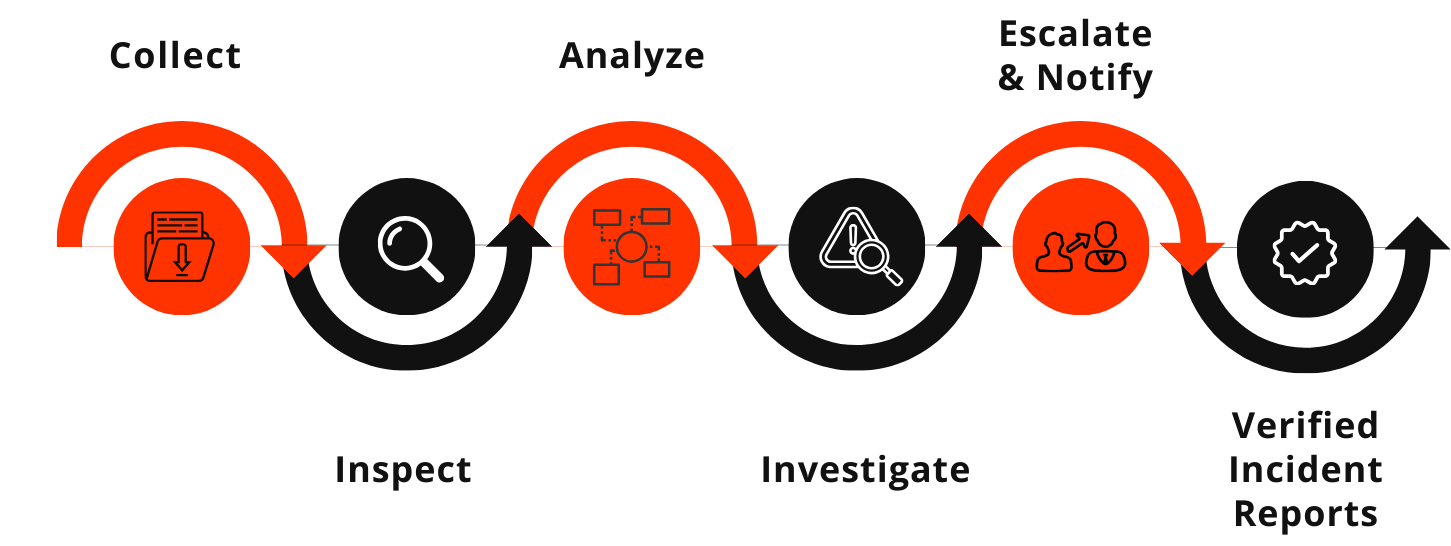
Command|MDR prioritizes threats based on their potential impact on your organization, reducing the time it takes your dedicated SOC analysts to process, investigate, and mitigate them. While ALL alerts are still reviewed, this prioritization approach allows analysts to focus on the most important threats first.

Level 1: Active Threat
Malicious actors have already established themselves in your environment

Level 2: Imminent Threat
A high-alert condition that exists just before a malicious actor gains access to your environment

Level 3: Interesting Items
The remaining alerts are interesting items to note, but they do not rise to the level of an "Active" or "Imminent" threat