Platform
Platform
Everything you need to run a secure global network—in a single system.
Solutions
Solutions
Learn how our solutions were designed to help you scale your IT resources
Company
CommandLink
Let's talk about how we can help you!
Partners
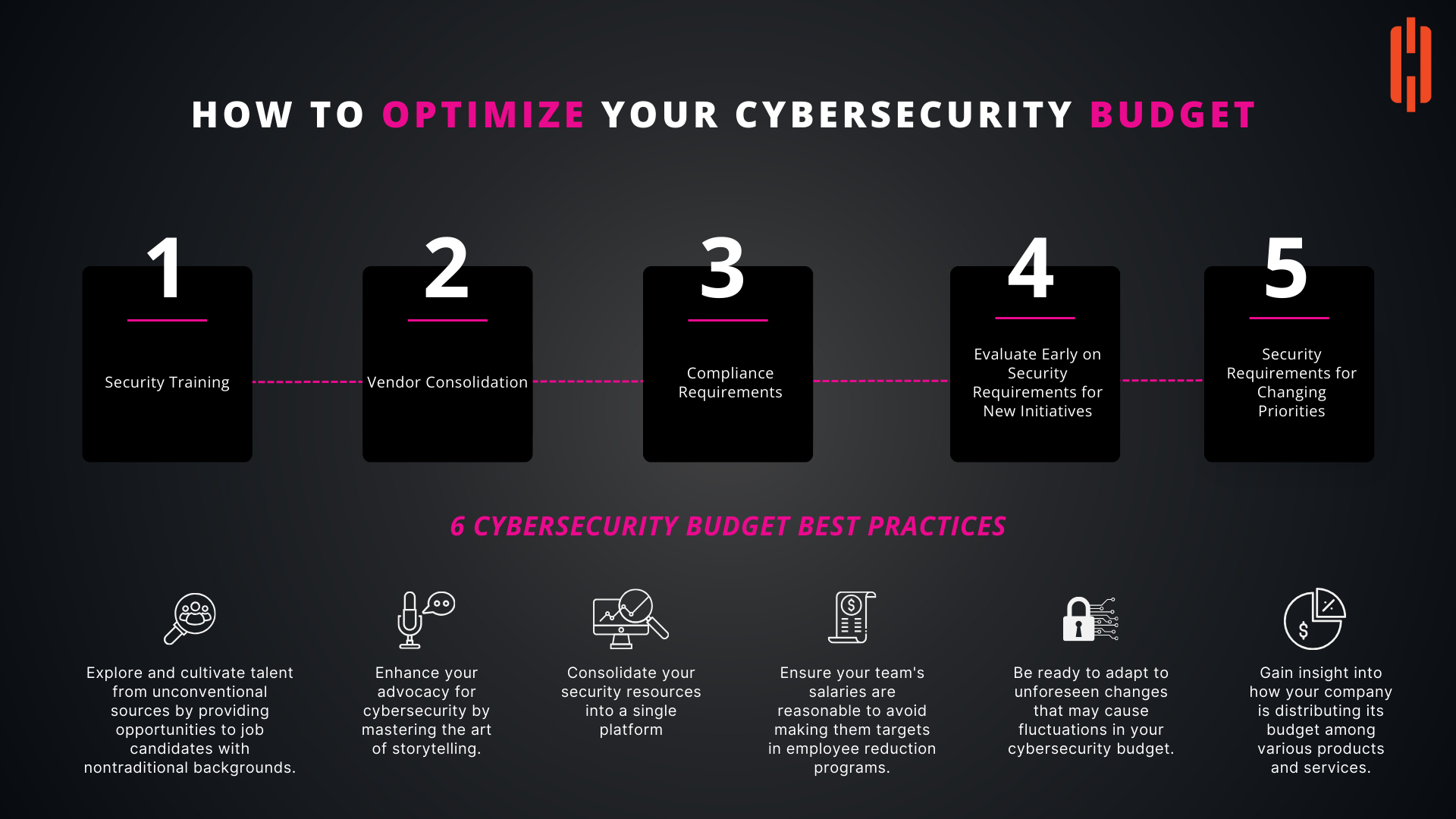
How to Optimize Your Cybersecurity Budget: Key Strategies and Best Practices
In the ever-evolving landscape of cybersecurity, organizations face the challenge of safeguarding their digital assets while efficiently managing their budgets. Optimizing your cybersecurity budget requires a strategic approach that balances the need for robust security measures with cost-effectiveness. This article explores essential strategies and best practices to help organizations make the most of their cybersecurity budgets.
What Are the Key Components of a Cybersecurity Budget?
Optimizing a cybersecurity budget begins with understanding its key components. These components typically include expenses related to security tools and technologies, personnel costs, training programs, compliance, and incident response planning. By identifying and categorizing these elements, organizations can prioritize spending on critical areas that directly contribute to their security posture.
Why Is Security Training Crucial for Budget Optimization?
Security training is a foundational element of an effective cybersecurity strategy. Investing in regular training programs for employees helps reduce human error, which is often a significant factor in security breaches. When employees are well-trained, they are less likely to fall victim to phishing attacks or other social engineering tactics, thereby reducing the likelihood of costly incidents. Prioritizing security training in your budget ensures that your workforce remains vigilant and knowledgeable about the latest threats.
How Can Vendor Consolidation Save Costs?
Vendor consolidation is another effective strategy for optimizing your cybersecurity budget. By reducing the number of vendors and streamlining the solutions used across the organization, you can negotiate better pricing and reduce administrative overhead. Consolidation also simplifies the management of security tools, making it easier to maintain a cohesive and integrated security environment. Organizations that successfully consolidate vendors often find that they can achieve the same level of security at a lower cost.
What Role Do Compliance Requirements Play in Budget Planning?
Compliance with industry regulations and standards is non-negotiable for most organizations. However, compliance-related expenses can be significant, particularly in highly regulated industries. To optimize your budget, it's essential to plan for these requirements early on and ensure that compliance initiatives are integrated into your overall security strategy. By doing so, you can avoid costly fines and penalties while ensuring that your organization meets its legal obligations.
Why Is Early Evaluation of Security Requirements Important for New Initiatives?
When launching new projects or initiatives, it's critical to evaluate security requirements early in the planning process. Doing so allows you to allocate budget resources efficiently and avoid unexpected expenses later on. By incorporating security considerations from the outset, you can design systems and processes that are secure by default, reducing the need for costly retrofits or emergency fixes.
How Can Organizations Adapt to Changing Security Priorities?
The cybersecurity landscape is dynamic, with new threats and vulnerabilities emerging regularly. As a result, organizations must be prepared to adapt their security strategies and budgets to address changing priorities. This flexibility requires a proactive approach to budget planning, where contingencies are built in for unforeseen events or shifts in the threat landscape. By regularly reviewing and adjusting your budget, you can ensure that your organization remains resilient in the face of evolving challenges.
What Are the Best Practices for Cybersecurity Budget Management?
To maximize the effectiveness of your cybersecurity budget, consider the following best practices:
By implementing these best practices, organizations can create a more efficient and effective cybersecurity budget that supports their overall security objectives while managing costs.