Platform
Platform
Everything you need to run a secure global network—in a single system.
Solutions
Solutions
Learn how our solutions were designed to help you scale your IT resources
Company
CommandLink
Let's talk about how we can help you!
Partners
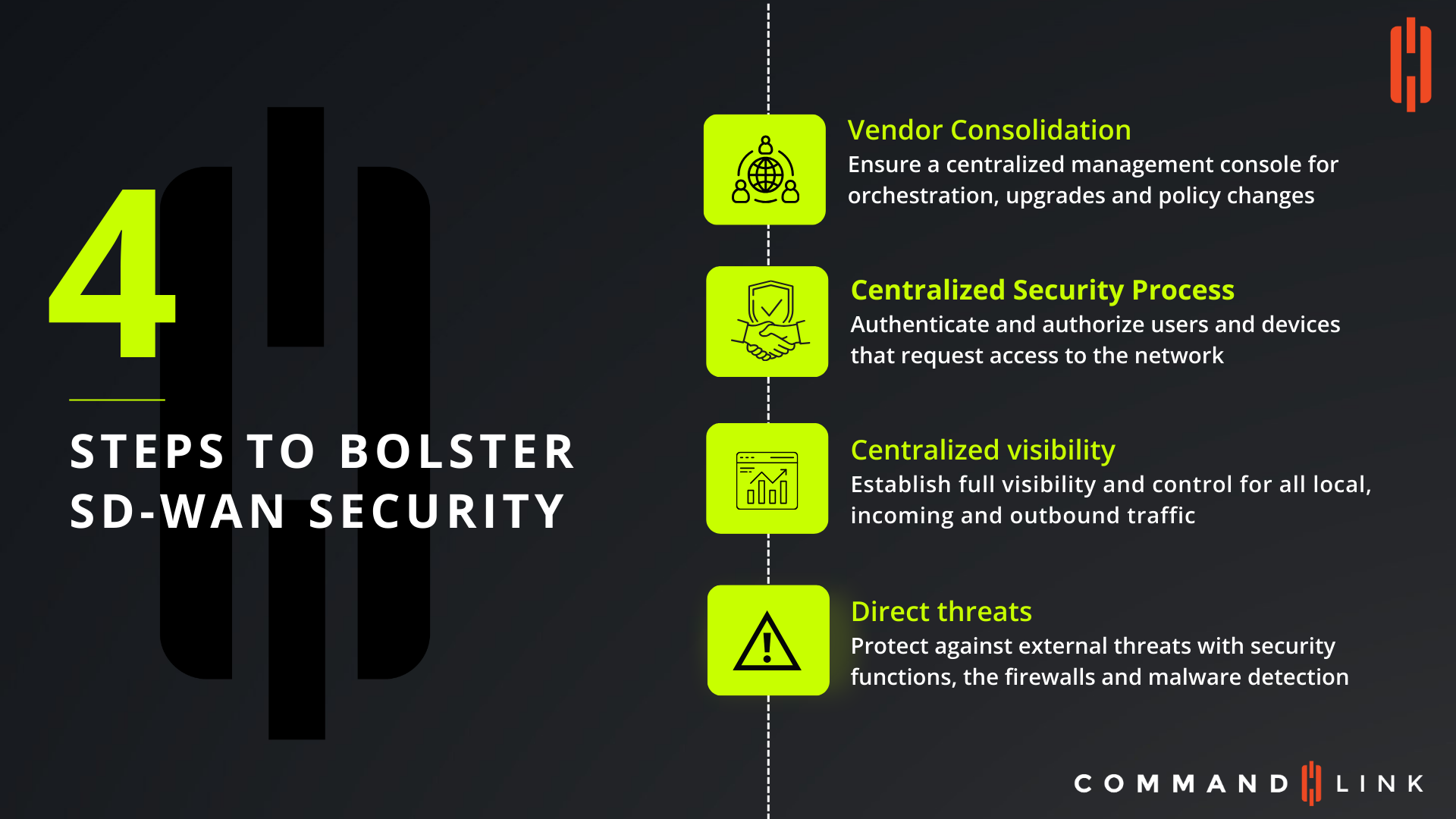
What Are the Essential Steps to Enhance SD-WAN Security?
As businesses increasingly adopt Software-Defined Wide Area Networks (SD-WAN) to optimize their networking infrastructure, ensuring robust security becomes paramount. SD-WAN's flexibility and efficiency can introduce vulnerabilities if not properly secured. Here, we outline four critical steps to bolster SD-WAN security and protect your network from potential threats.
Why Is Vendor Consolidation Important for SD-WAN Security?
One of the most effective ways to enhance SD-WAN security is through vendor consolidation. By ensuring that your SD-WAN solution is managed through a centralized console, you can streamline orchestration, upgrades, and policy changes. Consolidating vendors reduces the complexity of managing multiple security solutions, minimizes the risk of integration errors, and provides a unified approach to securing your network.
How Can a Centralized Security Process Strengthen SD-WAN?
Implementing a centralized security process is essential for authenticating and authorizing users and devices that request access to the network. This step involves establishing strict identity management protocols and ensuring that only trusted entities can access sensitive areas of your SD-WAN. Centralized security processes help prevent unauthorized access, mitigate insider threats, and ensure that all network activities are monitored and controlled.
What Role Does Centralized Visibility Play in SD-WAN Security?
Centralized visibility is crucial for maintaining comprehensive control over your SD-WAN environment. By establishing full visibility into all local, incoming, and outbound traffic, you can detect and respond to threats in real-time. Centralized visibility also allows for better analytics and reporting, enabling your security team to identify patterns, predict potential threats, and optimize network performance while maintaining security.
How Do You Protect SD-WAN from Direct Threats?
Protecting your SD-WAN from direct threats involves deploying security functions such as firewalls and malware detection systems. These tools act as the first line of defense against external threats, blocking malicious traffic and identifying vulnerabilities before they can be exploited. Regular updates and patching of these security functions are necessary to ensure they remain effective against evolving threats.