Platform
Platform
Everything you need to run a secure global network—in a single system.
Solutions
Solutions
Learn how our solutions were designed to help you scale your IT resources
Company
CommandLink
Let's talk about how we can help you!
Partners
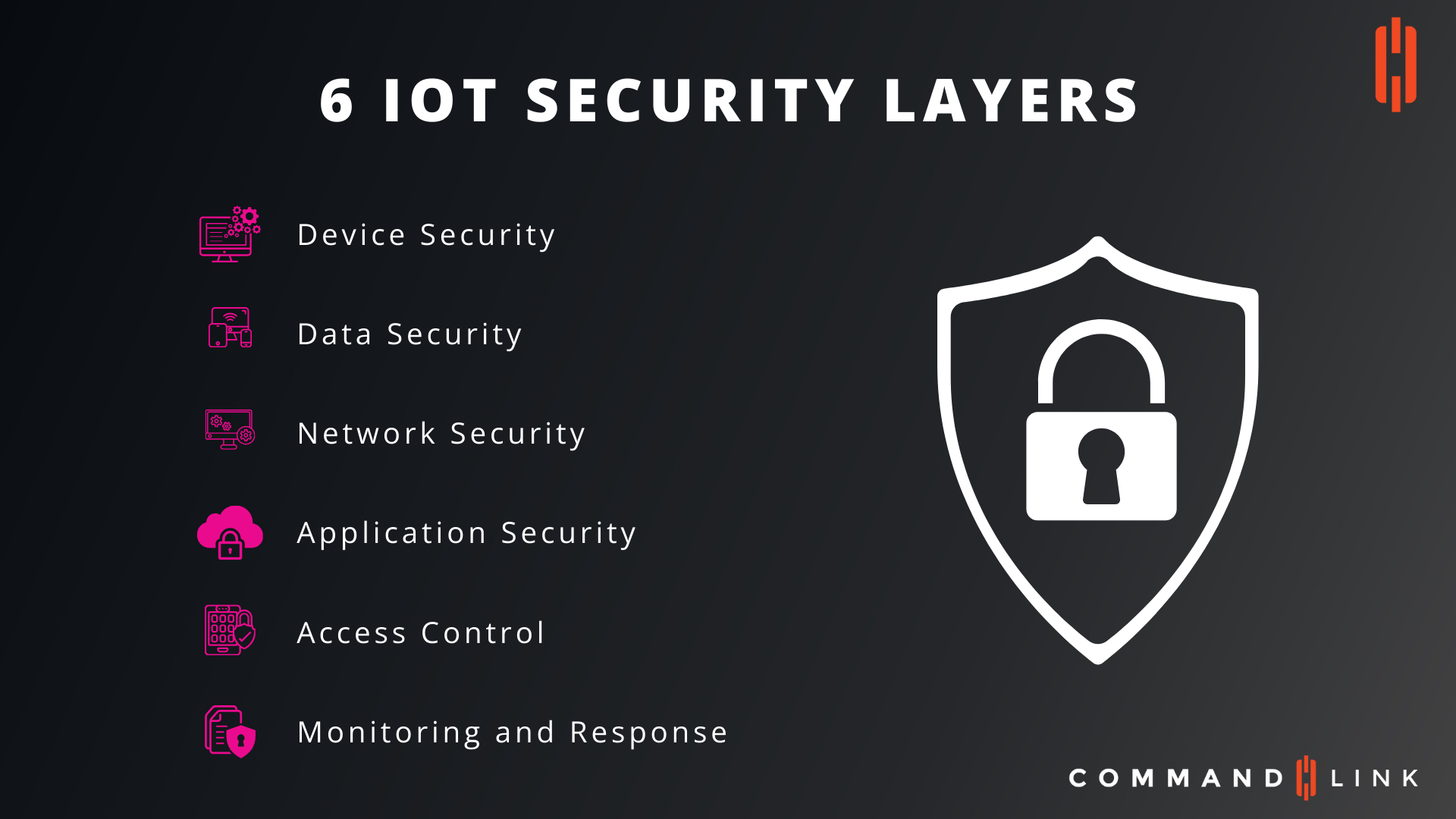
What Are the Key Security Layers in IoT?
The Internet of Things (IoT) is transforming industries by connecting billions of devices, but it also brings significant security challenges. To protect IoT ecosystems, it is essential to implement robust security measures across multiple layers. The six key security layers in IoT include Device Security, Data Security, Network Security, Application Security, Access Control, and Monitoring and Response.
How Can You Ensure Device Security in IoT?
Device Security is the foundation of IoT security. It involves securing the physical devices that connect to the IoT network. This includes using secure boot processes, hardware-based security features, and ensuring that devices are free from vulnerabilities that could be exploited by attackers. Regular firmware updates and patching are critical to maintaining the security of IoT devices.
Why Is Data Security Crucial in IoT?
Data Security is essential in IoT to protect sensitive information as it moves across networks and is stored in devices. This involves encrypting data both at rest and in transit to prevent unauthorized access and tampering. Implementing strong data protection measures ensures that even if data is intercepted, it cannot be read or altered by attackers.
What Role Does Network Security Play in IoT?
Network Security in IoT involves securing the communication channels between devices, gateways, and the cloud. This includes using secure protocols, implementing network segmentation, and employing firewalls and intrusion detection systems to protect against attacks. Network security ensures that the IoT infrastructure remains resilient against threats such as distributed denial-of-service (DDoS) attacks and unauthorized access.
How Is Application Security Implemented in IoT?
Application Security focuses on securing the software and applications that interact with IoT devices. This includes ensuring that applications are free from vulnerabilities such as code injection or buffer overflows. Regular security testing, such as static and dynamic analysis, helps identify and mitigate potential risks in IoT applications. By securing the application layer, organizations can prevent attackers from exploiting software weaknesses to gain access to the IoT network.
What Is the Importance of Access Control in IoT?
Access Control is a critical layer of IoT security that involves managing who has access to devices and data within the IoT ecosystem. Implementing strong authentication mechanisms, such as multi-factor authentication (MFA), and role-based access control (RBAC) ensures that only authorized users can access sensitive data and critical systems. Effective access control measures help prevent unauthorized access and reduce the risk of insider threats.
How Do Monitoring and Response Enhance IoT Security?
Monitoring and Response are essential for maintaining the security of IoT systems in real-time. Continuous monitoring involves tracking the activity of devices, networks, and applications to detect any suspicious behavior or potential threats. When an anomaly is detected, a rapid response is required to mitigate the impact of the threat. This may involve isolating compromised devices, blocking malicious traffic, or deploying patches. Effective monitoring and response capabilities are crucial for ensuring the ongoing security and integrity of IoT environments.