Platform
Platform
Everything you need to run a secure global network—in a single system.
Solutions
Solutions
Learn how our solutions were designed to help you scale your IT resources
Company
CommandLink
Let's talk about how we can help you!
Partners
What Is Penetration Testing and Why Is It Important?
Penetration testing, commonly known as pen testing, is a simulated cyber attack on a computer system, network, or web application to identify vulnerabilities that could be exploited by malicious hackers. The purpose of pen testing is to assess the security posture of an organization and to ensure that the defensive measures in place are effective in protecting against potential attacks. It is a critical component of a robust cybersecurity strategy, helping organizations to discover and remediate security weaknesses before they can be exploited.
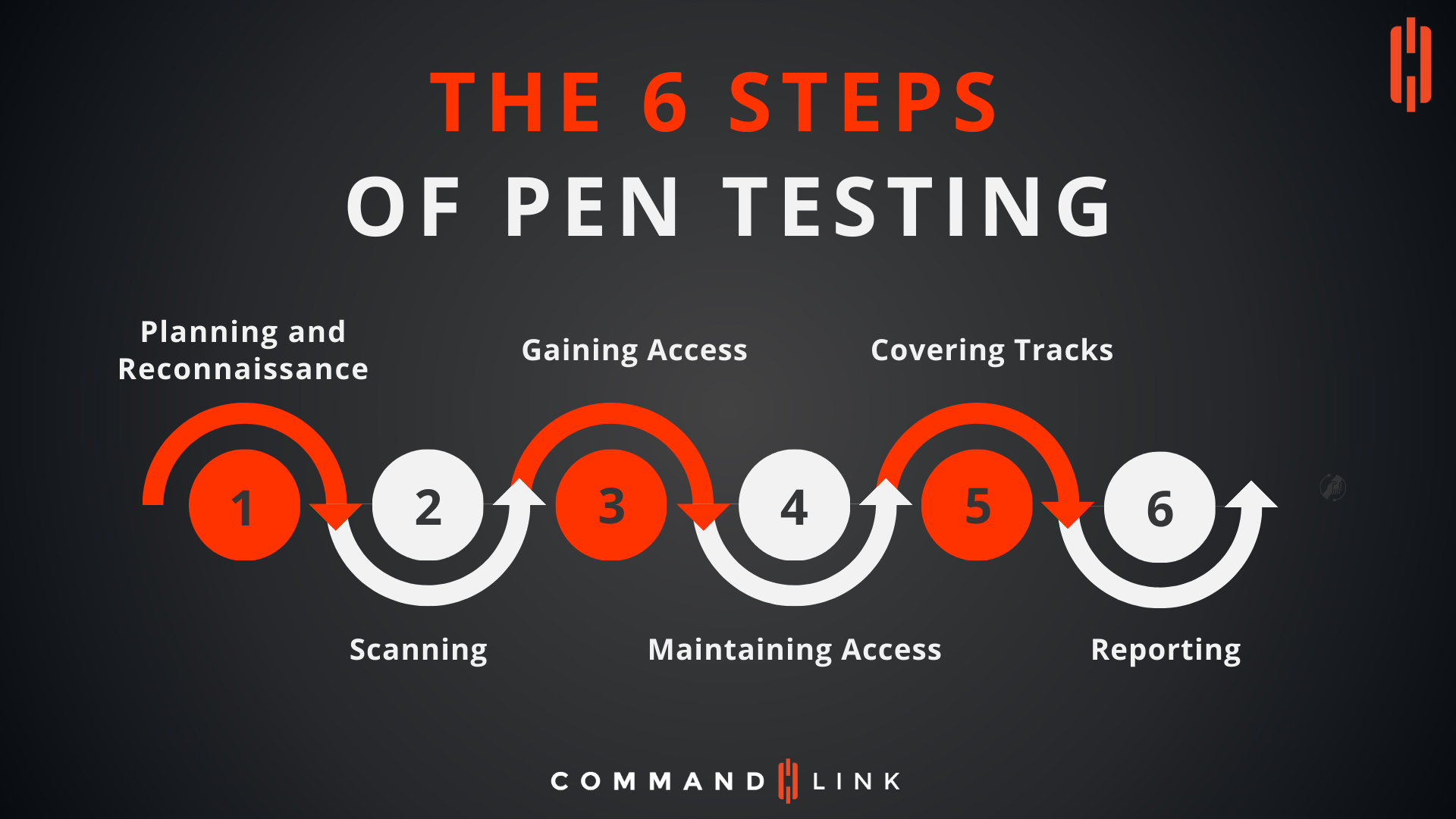
What Are the 6 Steps of Penetration Testing?
Penetration testing follows a systematic approach that typically consists of six steps:
Each of these steps plays a crucial role in conducting a thorough and effective pen test, ensuring that all potential vulnerabilities are identified and addressed.
What Happens During the Planning and Reconnaissance Stage?
The Planning and Reconnaissance stage is the first step in penetration testing, where the pen tester gathers as much information as possible about the target system. This includes understanding the target's infrastructure, identifying potential entry points, and determining the scope of the test. Reconnaissance can be passive, where the tester collects publicly available information, or active, where they interact directly with the target system to gather data. The goal of this stage is to develop a comprehensive plan for the pen test, including the tools and techniques that will be used.
Why Is Scanning Crucial in Pen Testing?
Scanning is the second step in the pen testing process, where the pen tester uses automated tools to identify vulnerabilities in the target system. This stage involves network scanning to detect open ports, services, and potential entry points, as well as vulnerability scanning to identify known security weaknesses. Scanning provides the pen tester with a detailed map of the target's infrastructure, highlighting areas that may be susceptible to attack.
How Do Pen Testers Gain Access to a Target System?
Gaining Access is the third step in pen testing, where the tester exploits identified vulnerabilities to gain control of the target system. This may involve techniques such as password cracking, exploiting software vulnerabilities, or using social engineering tactics. The goal of this stage is to demonstrate that the identified vulnerabilities can be exploited to gain unauthorized access to sensitive data or systems.
What Does Maintaining Access Mean in Pen Testing?
Maintaining Access refers to the fourth step in the pen testing process, where the tester ensures that they can maintain their foothold in the target system over an extended period. This may involve installing backdoors or other persistence mechanisms that allow the tester to remain undetected while continuing to gather information or further compromise the system. This stage is important because it simulates the actions of a real attacker who may want to stay within the network undetected for as long as possible.
Why Is Covering Tracks Important in Pen Testing?
Covering Tracks is the fifth step of pen testing, where the tester removes any traces of their activities to avoid detection. This involves clearing logs, deleting files, and undoing changes made to the system during the test. The purpose of this stage is to simulate the actions of a malicious actor who wants to remain undetected after carrying out an attack. It is a critical step in understanding how an attacker might cover their tracks to avoid detection by security teams.
What Should Be Included in a Pen Testing Report?
Reporting is the final step of the pen testing process, where the tester compiles their findings into a comprehensive report. The report should include details of all vulnerabilities identified, the methods used to exploit them, and the potential impact on the organization. It should also provide recommendations for remediation to help the organization strengthen its security posture. A well-documented report is essential for the organization to understand the results of the pen test and to take appropriate action to address any identified weaknesses.