Platform
Platform
Everything you need to run a secure global network—in a single system.
Solutions
Solutions
Learn how our solutions were designed to help you scale your IT resources
Company
CommandLink
Let's talk about how we can help you!
Partners
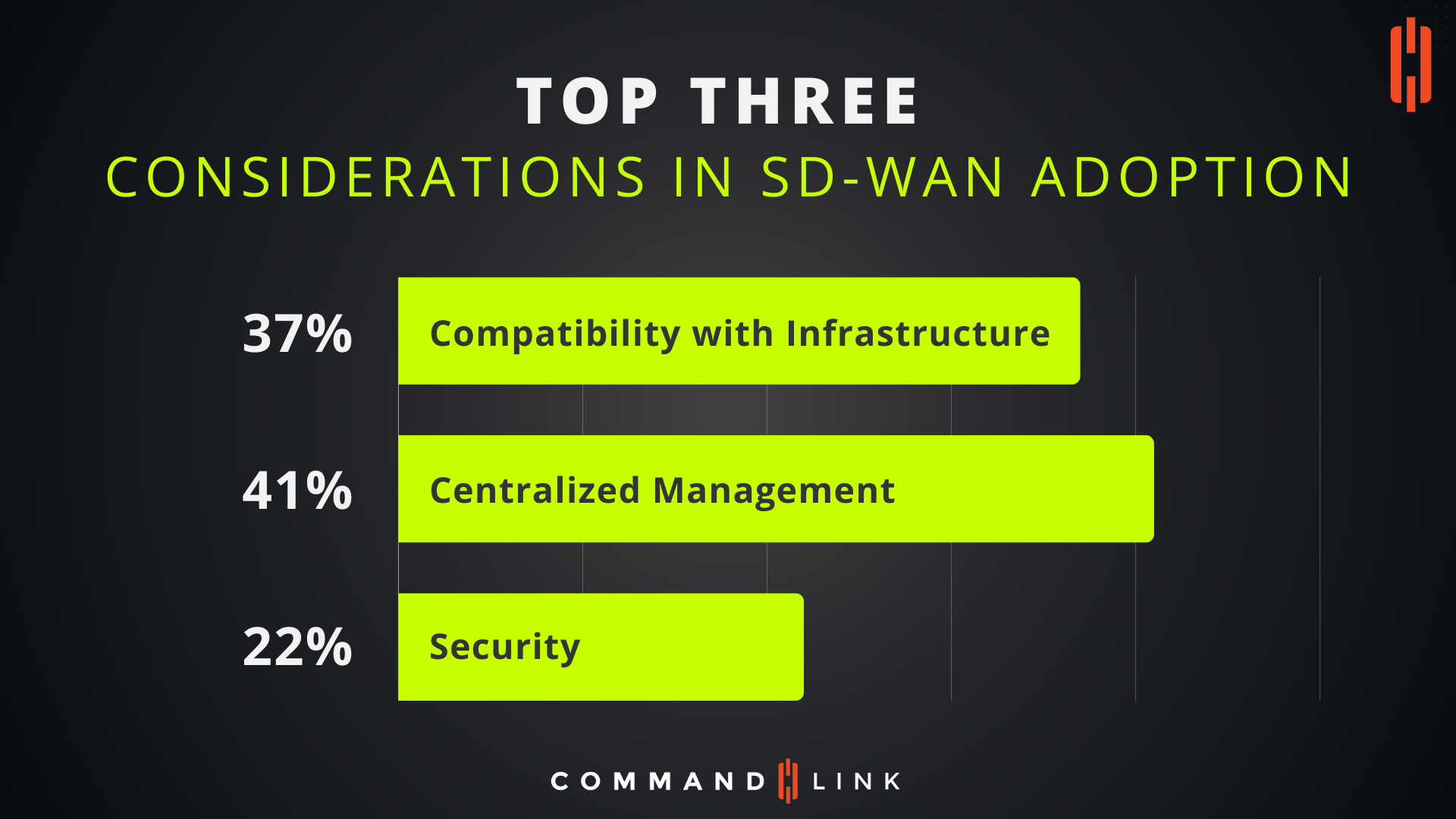
Why is Compatibility with Infrastructure a Critical Consideration in SD-WAN Adoption?
When adopting SD-WAN, one of the most crucial considerations for organizations is ensuring compatibility with their existing infrastructure. Compatibility is essential because it directly impacts the ease of deployment and the overall success of the SD-WAN implementation. Organizations typically have a mix of legacy systems, various network devices, and software that need to seamlessly integrate with the new SD-WAN solution. If the SD-WAN technology is not compatible with the existing infrastructure, it could lead to significant disruptions, increased costs, and extended deployment times. Therefore, it is vital for businesses to evaluate the compatibility of SD-WAN with their current network architecture, ensuring that the transition is as smooth as possible and that the new system can leverage existing investments without requiring a complete overhaul.
How Does Centralized Management Enhance the Effectiveness of SD-WAN?
Centralized management is another key consideration that significantly enhances the effectiveness of SD-WAN solutions. A centralized management platform provides IT teams with a single interface to manage, monitor, and control the entire network, regardless of its geographical distribution. This approach simplifies the complexities associated with managing traditional WANs, which often require managing multiple disparate systems. With centralized management, network administrators can easily implement policies, optimize traffic, and ensure consistent security across all locations. Additionally, centralized management facilitates real-time monitoring and rapid troubleshooting, allowing organizations to maintain high levels of performance and reliability across their networks. This efficiency not only reduces operational costs but also improves the responsiveness and agility of the IT team, making it easier to adapt to changing business needs.
Why is Security a Top Concern in SD-WAN Adoption?
Security is a paramount consideration in the adoption of SD-WAN, as the network perimeter becomes increasingly distributed and the threat landscape continues to evolve. Traditional WAN architectures were designed with a centralized security model, which is less effective in today’s cloud-centric environments where data and applications are accessed from multiple locations. SD-WAN addresses this by integrating advanced security features directly into the network fabric, ensuring that data is protected as it traverses the network. Features such as end-to-end encryption, secure tunneling, and integrated firewall capabilities are critical for safeguarding sensitive information and maintaining compliance with industry regulations. Furthermore, SD-WAN’s ability to segment network traffic and enforce security policies across all endpoints enhances the overall security posture of the organization. As cyber threats become more sophisticated, ensuring that SD-WAN solutions offer robust security measures is essential for protecting the integrity of the network and the data it carries.