Platform
Platform
Everything you need to run a secure global network—in a single system.
Solutions
Solutions
Learn how our solutions were designed to help you scale your IT resources
Company
CommandLink
Let's talk about how we can help you!
Partners
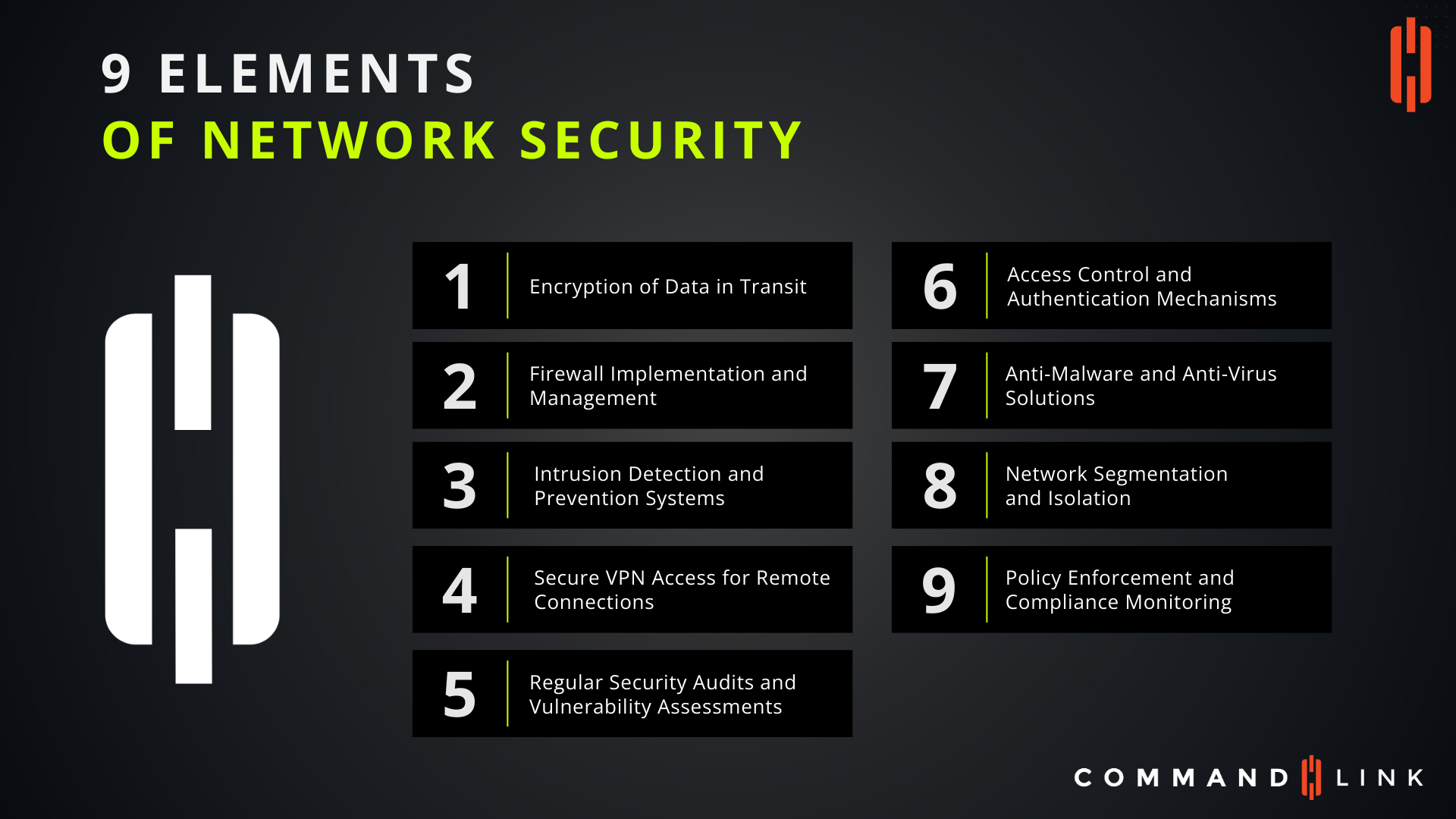
Why Is Encryption of Data in Transit Crucial for Network Security?
Encryption of data in transit is essential to protect sensitive information as it travels across networks. Without encryption, data can be intercepted by unauthorized parties, leading to breaches of confidentiality and integrity. By encrypting data, organizations ensure that even if data is intercepted, it remains unreadable and secure, thus preventing unauthorized access to sensitive information.
How Does Firewall Implementation and Management Enhance Network Protection?
Firewalls are the first line of defense in network security, controlling incoming and outgoing traffic based on predetermined security rules. Effective firewall implementation and management prevent unauthorized access to the network while allowing legitimate traffic. Regular updates and configuration checks are necessary to maintain firewall effectiveness and adapt to emerging threats.
What Role Do Intrusion Detection and Prevention Systems Play in Network Security?
Intrusion Detection and Prevention Systems (IDPS) monitor network traffic for suspicious activities and potential threats. These systems identify and respond to malicious activities in real-time, preventing security breaches before they can cause harm. IDPS is a critical component in network security, as it provides continuous monitoring and protection against evolving cyber threats.
Why Is Secure VPN Access Vital for Remote Connections?
Secure Virtual Private Network (VPN) access is essential for protecting data transmitted between remote users and the corporate network. VPNs encrypt the connection, ensuring that data remains secure even when accessed from unsecured locations, such as public Wi-Fi networks. Secure VPNs are crucial for maintaining the confidentiality and integrity of data in remote work environments.
How Do Regular Security Audits and Vulnerability Assessments Contribute to Network Security?
Regular security audits and vulnerability assessments are critical for identifying weaknesses in the network before they can be exploited. These assessments provide insights into the effectiveness of security controls, identify potential vulnerabilities, and help organizations stay ahead of threats. By conducting regular audits, organizations can continuously improve their security posture and mitigate risks.
What Are Access Control and Authentication Mechanisms, and Why Are They Important?
Access control and authentication mechanisms ensure that only authorized users can access network resources. These mechanisms include multi-factor authentication, role-based access controls, and strict password policies. By implementing robust access control and authentication, organizations can prevent unauthorized access, reduce the risk of insider threats, and protect sensitive data.
How Do Anti-Malware and Anti-Virus Solutions Safeguard Networks?
Anti-malware and anti-virus solutions detect, prevent, and remove malicious software from the network. These solutions are essential for protecting against a wide range of threats, including viruses, ransomware, and spyware. Regular updates and real-time scanning ensure that these solutions can respond to new and emerging threats, keeping the network secure from malware attacks.
Why Is Network Segmentation and Isolation a Key Security Strategy?
Network segmentation and isolation involve dividing a network into smaller, isolated segments to reduce the attack surface and limit the spread of threats. By isolating critical systems and data from the rest of the network, organizations can contain security incidents and prevent unauthorized access. Network segmentation is a proactive approach to minimizing the impact of security breaches.
How Does Policy Enforcement and Compliance Monitoring Strengthen Network Security?
Policy enforcement and compliance monitoring ensure that security policies are consistently applied across the network. This includes monitoring for compliance with industry standards, regulatory requirements, and internal security policies. By enforcing policies and monitoring compliance, organizations can reduce the risk of security breaches, avoid penalties, and maintain a strong security posture.