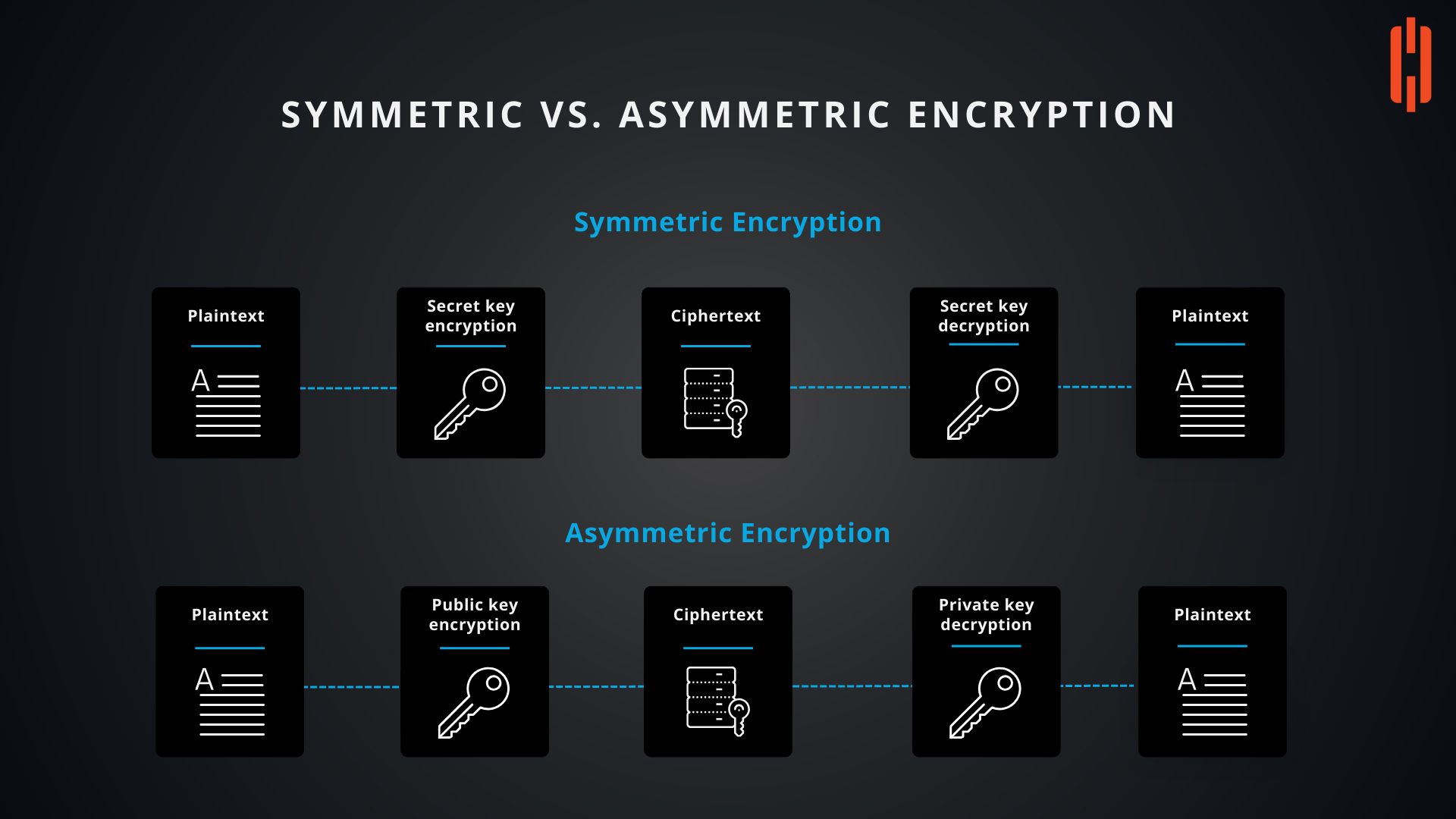
Symmetric Encryption
Symmetric encryption, also known as secret key encryption, is one of the oldest and most straightforward encryption methods. Here’s how it works:
Single Key Usage:
- Symmetric encryption uses a single key for both encryption and decryption of the data. This key must be shared between the sender and the receiver, which means both parties need to have access to the same secret key.
Process:
- Encryption: The sender uses the secret key to encrypt plaintext (the original data) into ciphertext (the encrypted data).
- Decryption: The receiver, who possesses the same secret key, uses it to decrypt the ciphertext back into plaintext.
Speed and Efficiency:
- Symmetric encryption is generally faster and more efficient than asymmetric encryption, making it well-suited for encrypting large amounts of data.
Security Considerations:
- The primary challenge with symmetric encryption lies in key management. Both parties must securely exchange and store the key, which, if compromised, would allow an attacker to decrypt the data.
Common Algorithms:
- Some widely used symmetric encryption algorithms include AES (Advanced Encryption Standard), DES (Data Encryption Standard), and 3DES (Triple DES).
Asymmetric Encryption
Asymmetric encryption, also known as public key encryption, is a more complex method that overcomes some of the limitations of symmetric encryption. Here’s how it works:
Two-Key System:
- Asymmetric encryption uses a pair of keys: a public key and a private key. The public key is used for encryption, and the private key is used for decryption. The two keys are mathematically linked, but it is computationally infeasible to derive the private key from the public key.
Process:
- Encryption: The sender encrypts the plaintext using the recipient’s public key, which is openly shared and accessible.
- Decryption: The recipient, who holds the corresponding private key, decrypts the ciphertext back into plaintext.
Security Advantage:
- One of the key advantages of asymmetric encryption is that it eliminates the need to share the private key, significantly reducing the risk of key compromise. The private key is kept secret by the owner, while the public key can be freely distributed.
Performance:
- Asymmetric encryption is generally slower and less efficient than symmetric encryption, making it less suitable for encrypting large volumes of data. However, it is often used for securing the exchange of symmetric keys (e.g., in SSL/TLS protocols) or for digital signatures.
Common Algorithms:
- Common asymmetric encryption algorithms include RSA (Rivest–Shamir–Adleman), ECC (Elliptic Curve Cryptography), and DSA (Digital Signature Algorithm).
When to Use Each Encryption Method
Symmetric Encryption:
- Best used in scenarios where speed and efficiency are critical, such as encrypting large datasets or securing communications in real-time applications. It’s also ideal when both parties can securely exchange the secret key.
Asymmetric Encryption:
- Ideal for situations where secure key exchange is required, such as in digital certificates, secure email communication (e.g., PGP/GPG), and in the initial stages of SSL/TLS connections where it is used to exchange symmetric keys securely.
Understanding the differences between symmetric and asymmetric encryption is crucial for selecting the appropriate method for securing data in various scenarios. Symmetric encryption offers speed and efficiency, making it suitable for bulk data encryption, while asymmetric encryption provides enhanced security for key exchange and authentication purposes. By leveraging the strengths of both methods, organizations can create robust encryption strategies that protect their sensitive information against unauthorized access.